A Comprehensive Look at Kerberos Authentication in Windows Server 2025: A Secure Foundation for Network Access
Related Articles: A Comprehensive Look at Kerberos Authentication in Windows Server 2025: A Secure Foundation for Network Access
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to A Comprehensive Look at Kerberos Authentication in Windows Server 2025: A Secure Foundation for Network Access. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
A Comprehensive Look at Kerberos Authentication in Windows Server 2025: A Secure Foundation for Network Access

The advancement of technology has ushered in an era of interconnectedness, where networks are the lifeblood of businesses and organizations. However, this interconnectedness also presents significant security challenges. The need for robust and secure authentication mechanisms has never been more critical. Enter Kerberos, a powerful authentication protocol that has long been a cornerstone of Windows Server security. As we look towards the future with Windows Server 2025, understanding the role and evolution of Kerberos becomes paramount.
Understanding the Fundamentals of Kerberos Authentication
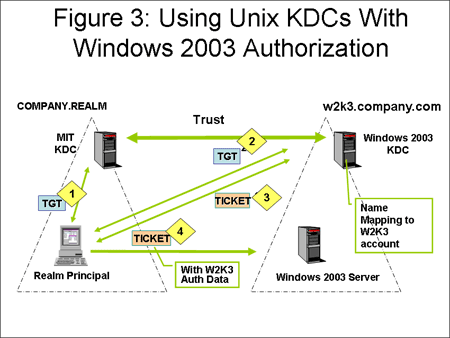
Kerberos, named after the Greek mythological three-headed dog who guards the gates of the underworld, operates on the principle of "mutual authentication." This means that both the client (user or device) and the server (resource being accessed) are verified before access is granted. The protocol employs a centralized authentication server, known as the Key Distribution Center (KDC), to manage the authentication process.
How Kerberos Works:
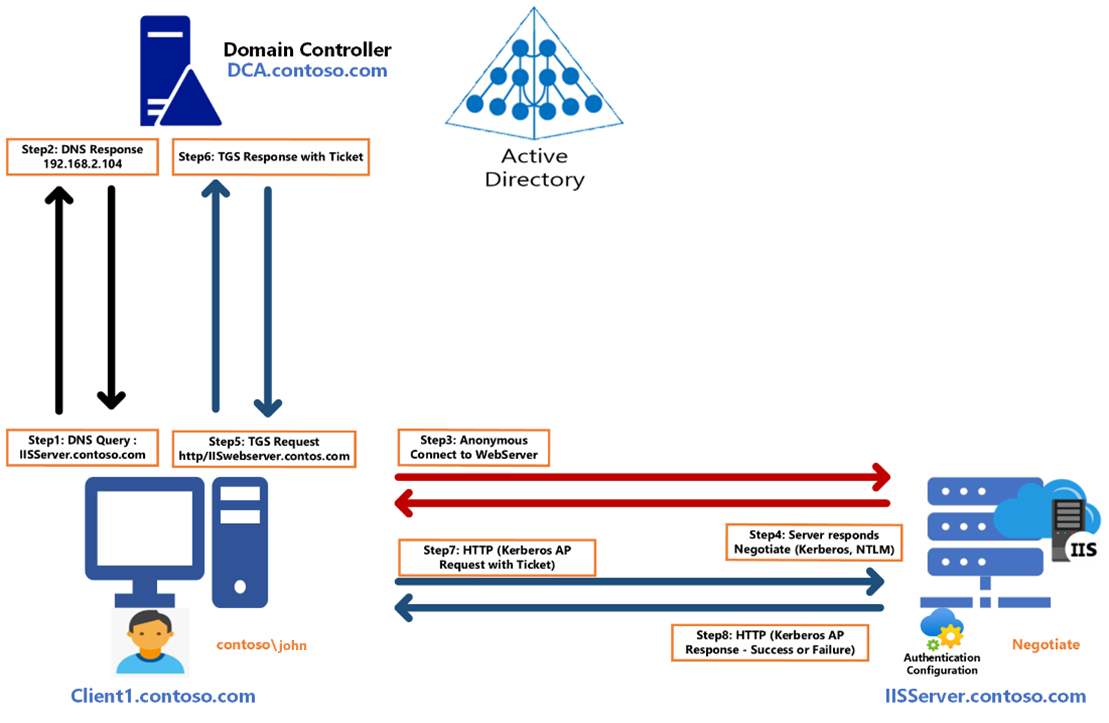
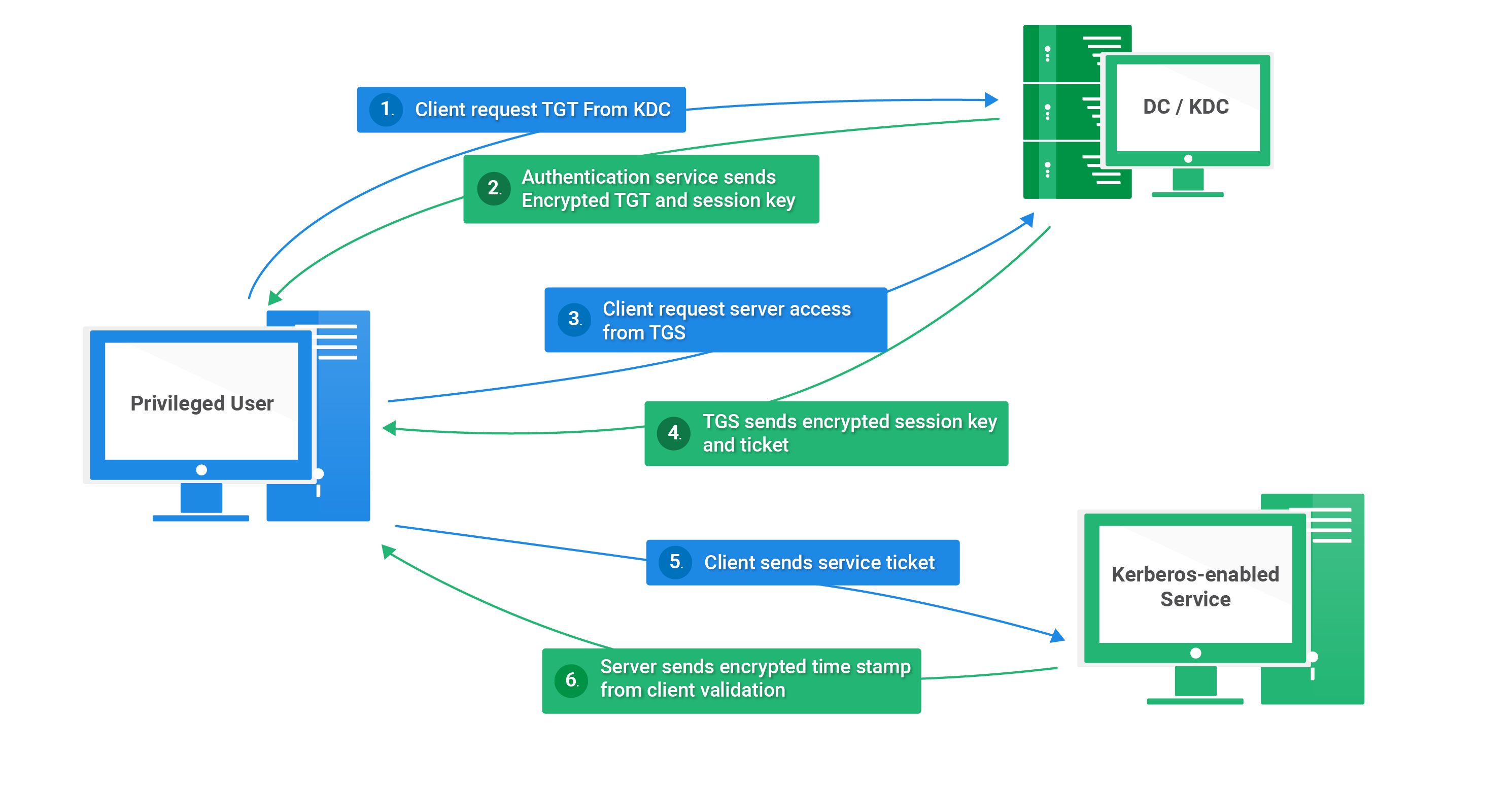
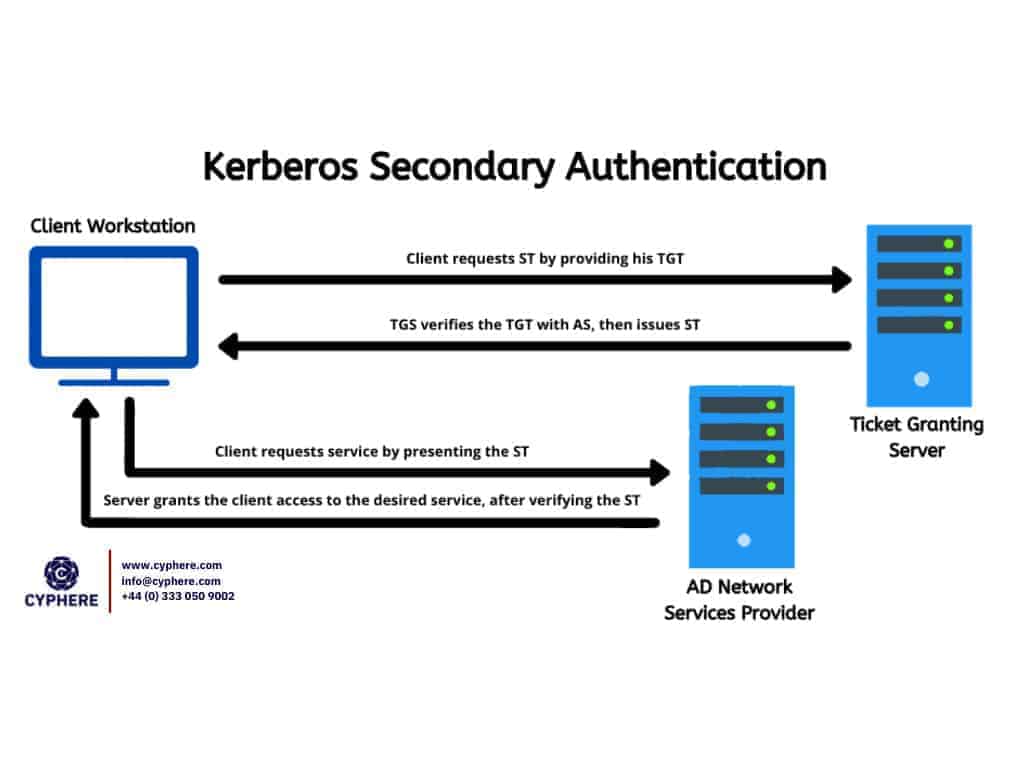
- Ticket Granting Ticket (TGT) Acquisition: When a user attempts to log in, their client sends a request to the KDC. The KDC verifies the user’s credentials and issues a TGT, a digital certificate that confirms the user’s identity.
- Service Ticket Acquisition: Armed with the TGT, the client can then request a service ticket from the KDC for a specific resource, such as a shared folder or an application. This ticket acts as a temporary password for the resource.
- Resource Access: The client presents the service ticket to the resource server. The server verifies the ticket with the KDC, and if validated, grants the client access to the resource.
Benefits of Kerberos Authentication in Windows Server 2025:
Kerberos offers several significant advantages, making it an indispensable security component in Windows Server 2025:
- Strong Authentication: Kerberos utilizes encryption and digital signatures throughout the authentication process, making it highly resistant to eavesdropping and tampering. This ensures the integrity and confidentiality of user credentials.
- Single Sign-On (SSO): Once a user is authenticated with their initial login, they can access various resources within the network without re-entering credentials. This simplifies user experience and improves productivity.
- Centralized Administration: The KDC provides a single point of control for managing user accounts, permissions, and authentication policies. This simplifies administrative tasks and enhances security management.
- Scalability and Flexibility: Kerberos is designed to handle large-scale deployments and can be integrated with various network services and applications.
- Enhanced Security Posture: Kerberos plays a vital role in securing sensitive data and resources, reducing the risk of unauthorized access and data breaches.
Evolution of Kerberos in Windows Server 2025:
While Kerberos has been a mainstay in Windows Server for years, its implementation continues to evolve to address new security challenges and enhance its capabilities. Windows Server 2025 is expected to further refine Kerberos with features like:
- Enhanced Key Management: Improved key management techniques will strengthen the security of the authentication process and make it more resilient against attacks.
- Support for Modern Authentication Protocols: Integration with modern authentication protocols like OAuth 2.0 and OpenID Connect will allow for seamless integration with cloud-based services and applications.
- Improved Performance and Scalability: Optimizations will ensure Kerberos can efficiently handle the increased demands of modern networks and handle large numbers of users and devices.
- Enhanced Security Auditing and Monitoring: Advanced auditing and monitoring capabilities will provide greater visibility into authentication events and help identify potential security threats.
Addressing Frequently Asked Questions (FAQs) about Kerberos in Windows Server 2025:
Q: Is Kerberos still relevant in a cloud-centric world?
A: Absolutely. While cloud services often have their own authentication mechanisms, Kerberos remains crucial for securing on-premises resources and hybrid environments. Kerberos can be integrated with cloud services using solutions like Azure Active Directory Domain Services (Azure AD DS).
Q: What are the potential security vulnerabilities associated with Kerberos?
A: While Kerberos is a robust protocol, it is not immune to vulnerabilities. Some potential security risks include:
- Password Guessing Attacks: Weak or easily guessable passwords can compromise Kerberos authentication.
- Man-in-the-Middle Attacks: Malicious actors can intercept communication between clients and the KDC, potentially stealing credentials.
- Replay Attacks: Attackers can capture and replay valid authentication tickets, gaining unauthorized access to resources.
Q: How can I mitigate these security risks?
A: To mitigate security risks associated with Kerberos, it is crucial to:
- Implement Strong Password Policies: Enforce strong password requirements, including length, complexity, and regular changes.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code.
- Use Secure Network Connections: Encrypt network traffic using protocols like TLS/SSL to protect against eavesdropping and man-in-the-middle attacks.
- Implement Security Monitoring and Auditing: Regularly monitor Kerberos logs and events for suspicious activity.
Q: What are some best practices for configuring and managing Kerberos in Windows Server 2025?
A:
- Utilize Group Policy Objects (GPOs): Configure Kerberos settings using GPOs to ensure consistency and ease of management.
- Implement Secure Kerberos Delegation: Use Kerberos delegation to allow services to authenticate to other resources on behalf of users.
- Regularly Patch and Update: Keep the Windows Server operating system and Kerberos components updated with the latest security patches.
- Perform Regular Security Audits: Regularly review Kerberos configuration and settings to identify potential vulnerabilities.
Tips for Implementing Kerberos in Windows Server 2025:
- Plan for a Secure and Scalable Deployment: Carefully plan your Kerberos deployment, considering the size of your network, the number of users and devices, and the types of resources you need to secure.
- Use a Dedicated Domain Controller for Kerberos: For optimal performance and security, dedicate a domain controller specifically for Kerberos operations.
- Implement Secure Kerberos Delegation: Leverage Kerberos delegation to grant services access to resources on behalf of users, ensuring secure and controlled access.
- Monitor Kerberos Events and Logs: Regularly review Kerberos logs and events for suspicious activity, enabling early detection of potential security threats.
- Test and Validate Your Configuration: Thoroughly test your Kerberos configuration to ensure it functions correctly and meets your security requirements.
Conclusion:
Kerberos authentication remains a cornerstone of security in Windows Server 2025. Its ability to provide strong, centralized, and scalable authentication makes it an essential component for securing networks and resources. By understanding the fundamentals of Kerberos, implementing best practices, and staying informed about its evolution, organizations can leverage this powerful protocol to build a secure and reliable foundation for their network access. As technology continues to evolve, Kerberos will undoubtedly play an even more crucial role in protecting sensitive data and enabling secure collaboration in the interconnected world of tomorrow.




Closure
Thus, we hope this article has provided valuable insights into A Comprehensive Look at Kerberos Authentication in Windows Server 2025: A Secure Foundation for Network Access. We appreciate your attention to our article. See you in our next article!
