Fortifying Windows Server: A Comprehensive Guide to Enhanced Security
Related Articles: Fortifying Windows Server: A Comprehensive Guide to Enhanced Security
Introduction
With great pleasure, we will explore the intriguing topic related to Fortifying Windows Server: A Comprehensive Guide to Enhanced Security. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Fortifying Windows Server: A Comprehensive Guide to Enhanced Security
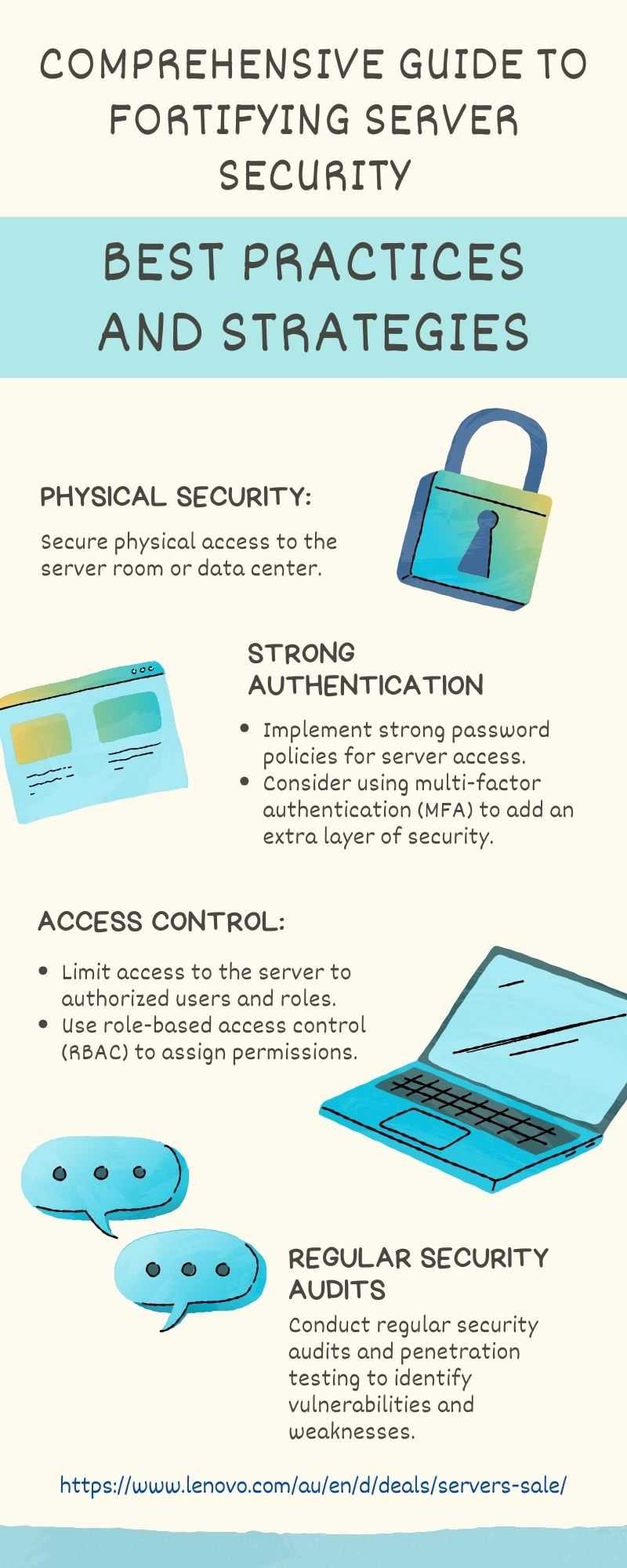
The digital landscape is constantly evolving, presenting new challenges and threats to organizations reliant on their IT infrastructure. Windows Server, a cornerstone of many businesses, requires a robust security posture to safeguard sensitive data and critical operations. This comprehensive guide delves into the multifaceted aspects of securing Windows Server, providing actionable insights and best practices to mitigate risks and ensure a fortified environment.
Understanding the Importance of Security
The significance of securing Windows Server cannot be overstated. A compromised server can lead to:
- Data Breaches: Unauthorized access to sensitive information, including customer data, financial records, and intellectual property.
- System Downtime: Disruptions to critical services, impacting business operations, productivity, and revenue.
- Financial Loss: Direct costs associated with data recovery, system restoration, and potential legal repercussions.
- Reputation Damage: Loss of trust and credibility among customers, partners, and stakeholders.
A Multi-Layered Approach to Server Security
Securing Windows Server is not a one-size-fits-all solution. It requires a comprehensive strategy encompassing multiple layers of protection:
1. Operating System Hardening:
- Regular Updates: Microsoft regularly releases security patches to address vulnerabilities. Implementing a strict update schedule ensures the server is protected against known exploits.
- Minimize Attack Surface: Disable unnecessary services, protocols, and features to reduce potential entry points for attackers.
- Strong Passwords and Policies: Enforce complex passwords, password rotation, and account lockout policies to prevent unauthorized access.
- Group Policy Management: Utilize Group Policy to configure security settings, restrict user privileges, and enforce consistent security practices across the server environment.
2. Network Security:
- Firewall Configuration: Implement a strong firewall to block unauthorized network traffic and control inbound and outbound connections.
- Network Segmentation: Isolate sensitive systems and data from public-facing networks to limit the impact of potential breaches.
- VPN and Secure Remote Access: Use Virtual Private Networks (VPNs) and secure remote access protocols to protect data transmitted over public networks.
- Network Intrusion Detection and Prevention Systems (IDS/IPS): Deploy IDS/IPS to monitor network traffic for suspicious activity and proactively block potential attacks.
3. Application Security:
- Secure Application Development Practices: Ensure applications are developed with security in mind, incorporating secure coding practices and vulnerability testing.
- Web Application Firewalls (WAFs): Utilize WAFs to protect web applications from common attacks, such as SQL injection and cross-site scripting.
- Regular Application Vulnerability Scans: Perform regular vulnerability scans to identify and address security weaknesses in applications.
- Least Privilege Principle: Grant applications only the minimum permissions required to perform their functions.
4. Data Protection:
- Data Encryption: Encrypt sensitive data at rest and in transit to protect it from unauthorized access even if the server is compromised.
- Data Backup and Recovery: Implement a robust backup and recovery strategy to ensure data can be restored in case of a disaster or security incident.
- Data Loss Prevention (DLP): Utilize DLP solutions to monitor and control sensitive data movement within and outside the organization.
5. Monitoring and Logging:
- Security Event Logging: Enable comprehensive logging of security events to provide a detailed audit trail and facilitate incident investigation.
- Security Information and Event Management (SIEM): Implement a SIEM solution to centralize security logs, analyze patterns, and detect potential threats.
- Regular Security Audits: Conduct periodic security audits to assess the effectiveness of security controls and identify areas for improvement.
6. User Education and Awareness:
- Security Awareness Training: Educate users about common security threats and best practices to prevent phishing attacks, malware infections, and other security incidents.
- Strong Password Practices: Encourage users to create strong passwords and avoid sharing them.
- Multi-Factor Authentication (MFA): Implement MFA for all user accounts to add an extra layer of security.
FAQs: Addressing Common Concerns
Q: What are the most common vulnerabilities in Windows Server?
A: Windows Server is susceptible to various vulnerabilities, including:
- Remote Code Execution (RCE): Allows attackers to execute arbitrary code on the server, potentially gaining full control.
- Denial of Service (DoS): Overloads the server with traffic, making it unavailable to legitimate users.
- Privilege Escalation: Allows attackers to gain elevated privileges on the server, enabling them to access sensitive data or modify system settings.
- Cross-Site Scripting (XSS): Allows attackers to inject malicious scripts into web applications, potentially stealing user credentials or data.
- SQL Injection: Allows attackers to manipulate database queries, potentially gaining access to sensitive information.
Q: How often should I update my Windows Server?
A: Microsoft releases security updates on a regular basis, typically on the second Tuesday of each month. It is highly recommended to install updates as soon as possible to mitigate vulnerabilities.
Q: How do I know if my Windows Server is secure?
A: There are several ways to assess the security of your Windows Server:
- Perform regular vulnerability scans: Use specialized tools to identify potential security weaknesses.
- Review security logs: Analyze security events to detect suspicious activity or potential breaches.
- Conduct security audits: Engage a security professional to evaluate your security posture and identify areas for improvement.
Tips for Effective Security Management
- Develop a comprehensive security policy: Document your security requirements, procedures, and responsibilities.
- Implement a layered security approach: Combine multiple security controls to create a robust defense.
- Regularly review and update your security practices: Stay informed about emerging threats and adapt your security strategy accordingly.
- Invest in security training for your staff: Educate your team about security best practices and how to identify and report potential threats.
- Consider professional security services: Engage security experts to provide ongoing security assessments, incident response, and other specialized services.
Conclusion: Building a Strong Security Foundation
Securing Windows Server is an ongoing process that requires vigilance and continuous improvement. By implementing a multi-layered security strategy, adhering to best practices, and staying informed about emerging threats, organizations can build a strong security foundation to protect their critical data and operations. Investing in security is an investment in business continuity, data integrity, and overall organizational resilience.






Closure
Thus, we hope this article has provided valuable insights into Fortifying Windows Server: A Comprehensive Guide to Enhanced Security. We hope you find this article informative and beneficial. See you in our next article!
