Implementing Active Directory Federation Services (AD FS) on Windows Server 2022: A Comprehensive Guide
Related Articles: Implementing Active Directory Federation Services (AD FS) on Windows Server 2022: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Implementing Active Directory Federation Services (AD FS) on Windows Server 2022: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Implementing Active Directory Federation Services (AD FS) on Windows Server 2022: A Comprehensive Guide
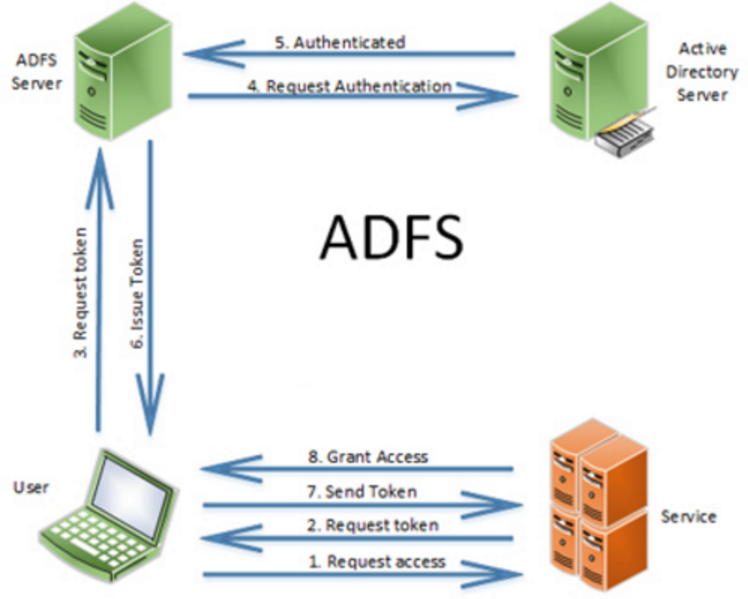
Active Directory Federation Services (AD FS) is a crucial component of modern identity and access management (IAM) strategies, offering a robust and secure method for federated authentication and authorization across diverse applications and services. This guide delves into the process of setting up AD FS on Windows Server 2022, providing a detailed understanding of its functionalities, configuration steps, and best practices.
Understanding AD FS: A Foundation for Secure Identity Management
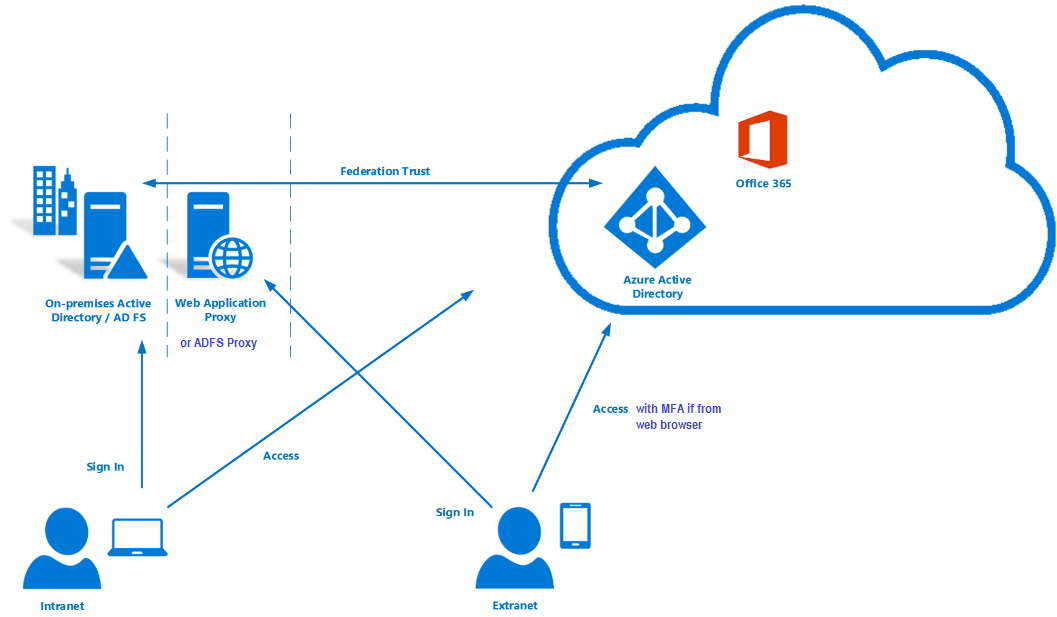
AD FS serves as a central identity provider, enabling users to access various applications and resources with a single set of credentials. It accomplishes this through the concept of federation, where trust relationships are established between AD FS and relying parties (applications or services that rely on AD FS for authentication). This approach simplifies the management of user identities and streamlines access control, reducing administrative overhead and enhancing security.
The Benefits of Implementing AD FS
- Single Sign-On (SSO): Users can access multiple applications with a single login, improving user experience and productivity.
- Enhanced Security: AD FS strengthens security by centralizing authentication and authorization, enforcing robust security policies and providing granular access control.
- Simplified Identity Management: AD FS simplifies the management of user identities, reducing the need for multiple accounts and passwords.
- Federated Identity Management: AD FS enables organizations to collaborate with external partners and customers securely by establishing trust relationships.
- Support for Modern Authentication Protocols: AD FS supports industry-standard protocols like SAML, OAuth, and OpenID Connect, ensuring compatibility with diverse applications and services.
Prerequisites for AD FS Deployment
Before embarking on the AD FS setup process, ensure the following prerequisites are met:
- Windows Server 2022: AD FS requires a Windows Server 2022 operating system.
- Active Directory Domain Services (AD DS): A functional AD DS environment is essential for managing user identities and group policies.
- Public Certificate: A valid public certificate is required for AD FS to establish secure communication with relying parties.
- Network Connectivity: Ensure the AD FS server has network connectivity to both internal and external resources.
- Database: AD FS requires a SQL Server database for storing configuration data and user information.
Setting Up AD FS on Windows Server 2022
The following steps outline the process of installing and configuring AD FS on Windows Server 2022:
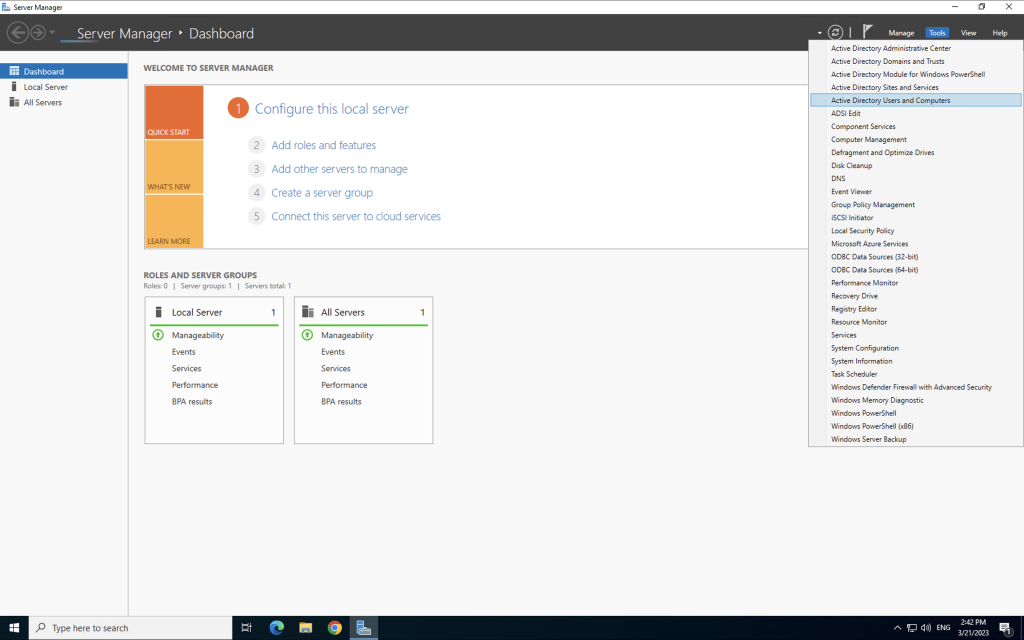
- Install the AD FS Role: Begin by installing the AD FS role on the designated server. This can be achieved through the Server Manager interface or using PowerShell commands.
- Configure the AD FS Farm: If you require high availability or load balancing, configure a farm of AD FS servers. This involves creating a federation service and adding multiple servers to the farm.
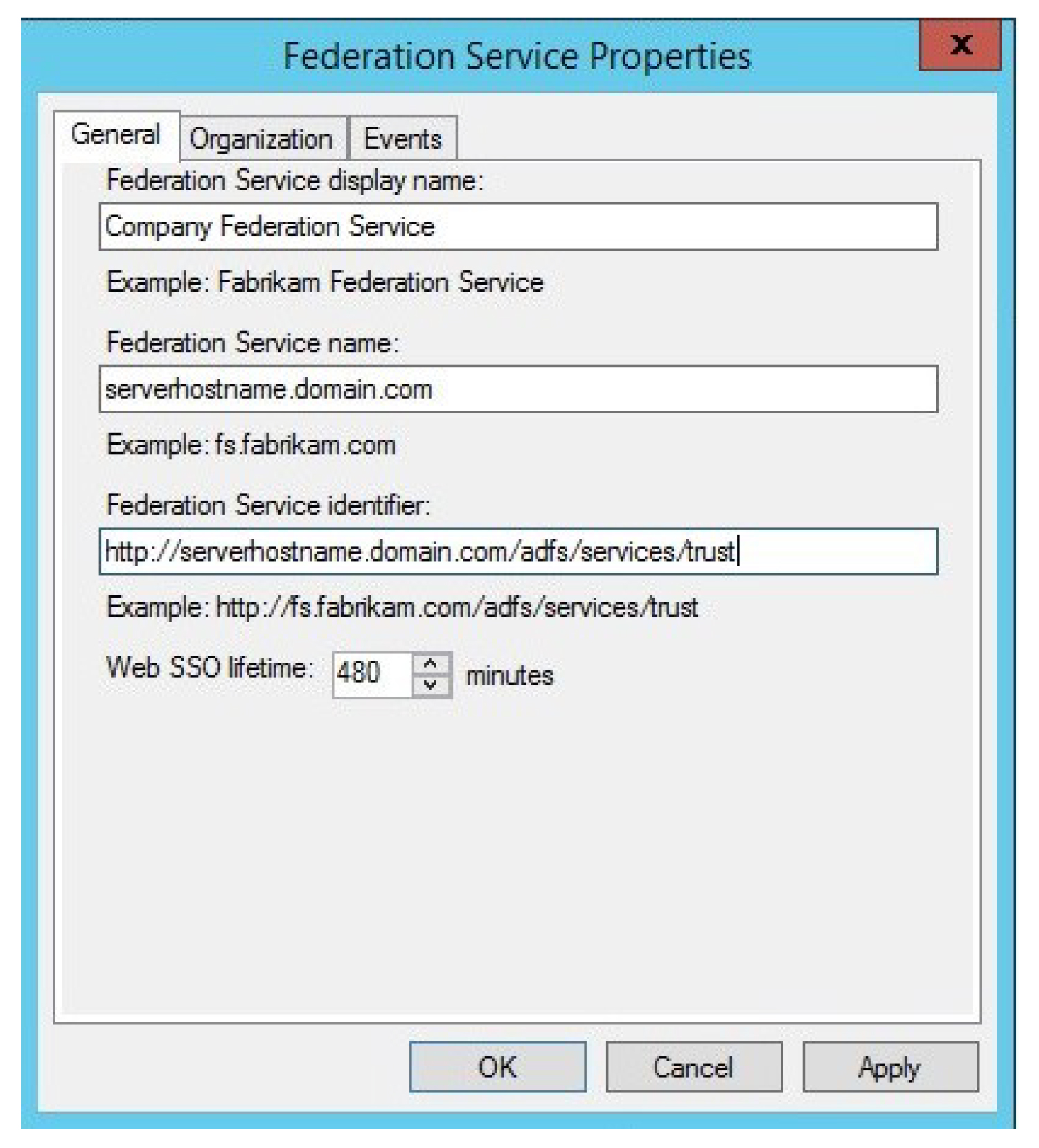
- Configure the Federation Service: During the AD FS configuration process, you will define the federation service name, specify the certificate for secure communication, and configure the database connection.
- Create Relying Party Trusts: Define the trust relationships between AD FS and relying parties. This involves adding the relying party’s metadata, configuring authentication policies, and specifying the claims to be sent to the relying party.
- Configure Claims Rules: Define the rules for mapping user attributes (like user name, email address, and group memberships) to claims that will be sent to relying parties.
- Test and Deploy: After configuring AD FS, test the setup by accessing a relying party application using a federated identity. Once validated, deploy the AD FS service to your production environment.
Key Considerations for AD FS Deployment
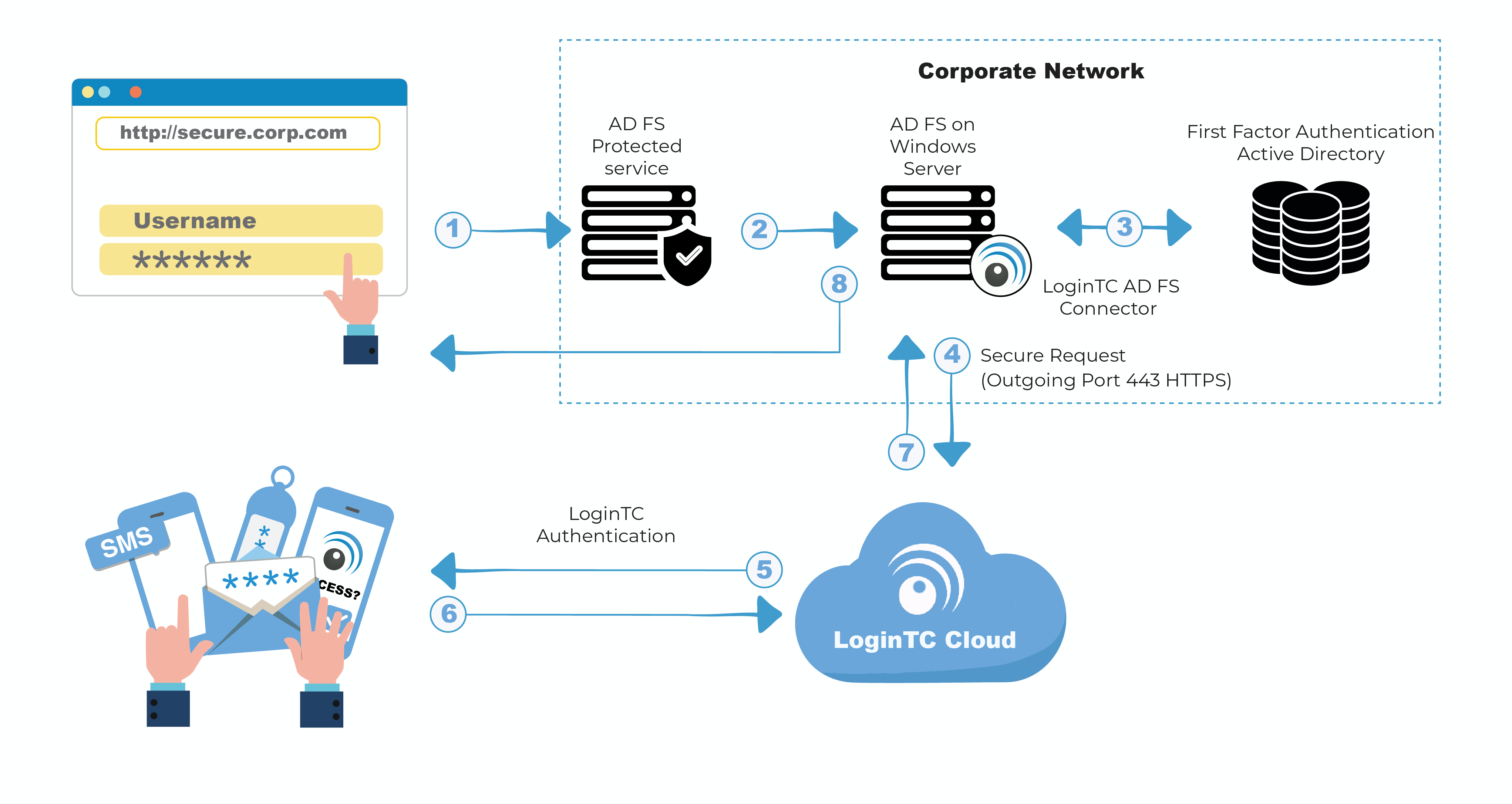
- Security: Implementing strong security measures is paramount. This includes configuring access control policies, enabling multi-factor authentication (MFA), and regularly updating AD FS and its dependencies.
- Scalability: Plan for future growth by considering the scalability of the AD FS infrastructure. Ensure sufficient server resources and database capacity to accommodate increasing user base and application access.
- Monitoring and Logging: Implement comprehensive monitoring and logging mechanisms to track AD FS activity, identify security events, and diagnose issues proactively.
- Documentation: Maintain detailed documentation of the AD FS configuration, including relying party trusts, claims rules, and security settings. This will facilitate troubleshooting and future maintenance.
Frequently Asked Questions (FAQs)
Q: What are the different ways to configure AD FS authentication methods?
A: AD FS offers a range of authentication methods, including:
- Forms-Based Authentication: Users provide their credentials through a web form.
- Windows Integrated Authentication: Users are automatically authenticated using their domain credentials.
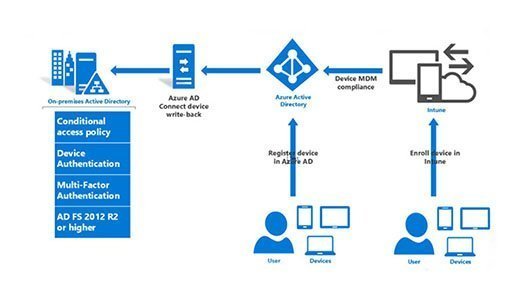
- Password Hash Synchronization: Passwords are synchronized with a cloud-based identity provider like Azure Active Directory.
- Multi-Factor Authentication (MFA): Users are required to provide additional authentication factors, such as a one-time code or biometric verification.
Q: How do I manage user identities in AD FS?
A: User identities in AD FS are typically managed through Active Directory Domain Services (AD DS). AD FS relies on AD DS for user information, group memberships, and authentication data.
Q: Can AD FS be used for single sign-on (SSO) across multiple domains?
A: Yes, AD FS can be used for SSO across multiple domains by establishing trust relationships between the domains.
Q: What are the security best practices for AD FS?
A: Implementing strong security practices is crucial for securing AD FS:
- Enable MFA: Use multi-factor authentication to enhance security and prevent unauthorized access.
- Secure the AD FS Server: Implement robust access control policies, disable unnecessary services, and regularly update the operating system and AD FS software.
- Monitor and Audit: Continuously monitor AD FS activity, review audit logs, and investigate suspicious events.
- Use Strong Passwords: Enforce strong password policies for user accounts and administrative credentials.
Tips for Successful AD FS Deployment
- Plan Carefully: Define your organization’s identity and access management requirements before deploying AD FS.
- Test Thoroughly: Thoroughly test the AD FS setup and configuration before deploying it to production.
- Document Everything: Maintain detailed documentation of your AD FS configuration and security settings.
- Stay Updated: Regularly update AD FS and its dependencies to address security vulnerabilities and enhance functionality.
Conclusion
Implementing AD FS on Windows Server 2022 provides a robust and secure solution for managing user identities and controlling access to applications and services. By understanding the concepts of federation, configuring the AD FS service, and following best practices, organizations can leverage the power of AD FS to enhance security, simplify identity management, and improve user experience. As technology evolves, AD FS will continue to play a pivotal role in modern identity and access management strategies, enabling organizations to navigate the complexities of digital security with confidence.


Closure
Thus, we hope this article has provided valuable insights into Implementing Active Directory Federation Services (AD FS) on Windows Server 2022: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!
