Navigating the Landscape of Server 2025 TPM Requirements: A Comprehensive Guide
Related Articles: Navigating the Landscape of Server 2025 TPM Requirements: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Landscape of Server 2025 TPM Requirements: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Landscape of Server 2025 TPM Requirements: A Comprehensive Guide
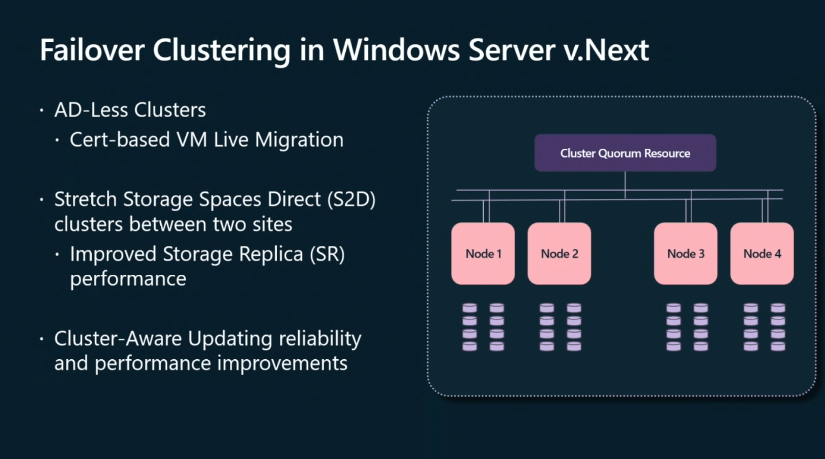
The advent of Windows Server 2025 marks a significant shift in the security landscape for organizations. With the introduction of new security features and enhanced security protocols, a critical component of this evolution is the requirement for Trusted Platform Module (TPM) 2.0 support. This guide aims to demystify the intricacies of TPM 2.0 within the context of Server 2025, offering a comprehensive understanding of its significance, benefits, and implementation considerations.
Understanding the Role of TPM 2.0 in Server 2025
The Trusted Platform Module (TPM) is a hardware chip embedded within a computer system, serving as a dedicated cryptographic processor. It functions as a secure vault, safeguarding sensitive data and cryptographic keys. In the context of Server 2025, the TPM 2.0 standard plays a pivotal role in bolstering security measures, enhancing data integrity, and mitigating potential threats.
Key Benefits of TPM 2.0 in Server 2025
1. Secure Boot and System Integrity: TPM 2.0 acts as a gatekeeper, ensuring that only trusted operating systems and applications can load on the server. This prevents malicious software from compromising the system before the operating system even starts, significantly enhancing boot security.
2. Enhanced Encryption and Data Protection: TPM 2.0 allows for hardware-based encryption, further protecting sensitive data stored on the server. This encryption is independent of the operating system, making it more resilient to attacks targeting software vulnerabilities.
3. Secure Storage of Credentials and Keys: TPM 2.0 provides a secure environment for storing cryptographic keys, passwords, and other sensitive credentials. This prevents unauthorized access and safeguards against potential breaches.
4. Support for Advanced Security Features: TPM 2.0 enables the use of advanced security features like BitLocker Drive Encryption, Virtual Secure Mode (VSM), and Device Guard, which further strengthen the server’s security posture.
5. Compliance with Industry Standards and Regulations: With increasing regulatory requirements around data security, TPM 2.0 compliance is crucial for meeting industry standards and regulations like PCI DSS, HIPAA, and GDPR.
Navigating TPM 2.0 Compatibility and Implementation
1. Server Hardware Compatibility: The first step is ensuring your server hardware supports TPM 2.0. Most modern server platforms released in recent years are likely to have TPM 2.0 built-in. Consult the server manufacturer’s documentation to verify compatibility.
2. BIOS Configuration: Once you have a TPM 2.0-enabled server, you need to enable it in the BIOS settings. This usually involves navigating to the security or advanced settings menu and activating the TPM module.
3. Windows Server 2025 Configuration: After enabling the TPM in the BIOS, you need to configure it within Windows Server 2025. This involves using tools like the "tpm.msc" console to manage the TPM, set security policies, and enable features like BitLocker.
4. Enabling Secure Boot: Secure Boot is a security feature that leverages the TPM to ensure only trusted software loads on the server. It’s generally recommended to enable Secure Boot alongside TPM 2.0 for enhanced security.
5. Managing TPM Keys and Certificates: TPM 2.0 enables the generation and storage of cryptographic keys. Organizations need to implement robust key management practices, ensuring secure storage and rotation of keys to maintain security.
Addressing Common Concerns and FAQs
1. Is TPM 2.0 mandatory for Server 2025? While not strictly mandatory, the absence of TPM 2.0 will limit access to certain security features and may hinder compliance with industry standards. It is highly recommended to utilize TPM 2.0 for optimal security and compliance.
2. How do I know if my server has TPM 2.0? Consult the server manufacturer’s documentation or use tools like the "tpm.msc" console in Windows to check for TPM presence and version.
3. Can I upgrade an older server to TPM 2.0? While some older servers may have TPM 1.2 modules, upgrading to TPM 2.0 is generally not possible. Consider upgrading to a newer server with built-in TPM 2.0 support for enhanced security.
4. What are the security implications of not using TPM 2.0? Without TPM 2.0, your server will be more susceptible to boot-time attacks, vulnerabilities in the operating system, and unauthorized data access. It will also limit your ability to utilize advanced security features like BitLocker and Device Guard.
5. What are the best practices for managing TPM 2.0? Implement robust key management practices, regularly update firmware and drivers, and monitor for potential security threats.
Tips for Implementing TPM 2.0 in Server 2025
1. Plan Ahead: Before deploying Server 2025, ensure your server hardware and BIOS support TPM 2.0. Consult the manufacturer’s documentation and perform thorough testing to ensure compatibility.
2. Secure BIOS Configuration: Configure the BIOS settings to enable the TPM module and set appropriate security policies. This includes enabling Secure Boot and setting password protections for accessing the TPM.
3. Implement Key Management Practices: Establish a robust key management system for storing, rotating, and managing cryptographic keys generated by the TPM.
4. Regular Security Audits: Conduct regular security audits to assess the health of the TPM and identify any potential vulnerabilities or security issues.
5. Stay Updated: Regularly update the firmware, drivers, and operating system to address security vulnerabilities and ensure compatibility with the latest TPM 2.0 standards.
Conclusion
The integration of TPM 2.0 in Server 2025 represents a significant advancement in server security. By leveraging the power of hardware-based security, TPM 2.0 strengthens data protection, enhances system integrity, and enables the use of advanced security features. Implementing TPM 2.0 effectively requires careful planning, thorough configuration, and a commitment to ongoing security best practices. By embracing this technology, organizations can significantly enhance their security posture, safeguard sensitive data, and meet evolving compliance requirements in the digital landscape.



Closure
Thus, we hope this article has provided valuable insights into Navigating the Landscape of Server 2025 TPM Requirements: A Comprehensive Guide. We appreciate your attention to our article. See you in our next article!
