Secure Shell (SSH) Server on Windows Server 2025: A Comprehensive Guide
Related Articles: Secure Shell (SSH) Server on Windows Server 2025: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Secure Shell (SSH) Server on Windows Server 2025: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Secure Shell (SSH) Server on Windows Server 2025: A Comprehensive Guide

The introduction of SSH servers on Windows platforms signifies a significant shift in the landscape of remote administration and secure communication. While traditionally associated with Linux and Unix environments, SSH has emerged as a robust and widely adopted protocol for secure remote access and data transfer on Windows Server operating systems. This article delves into the intricacies of SSH server implementation on Windows Server 2025, exploring its functionalities, benefits, and practical considerations.
Understanding SSH: A Foundation for Secure Communication
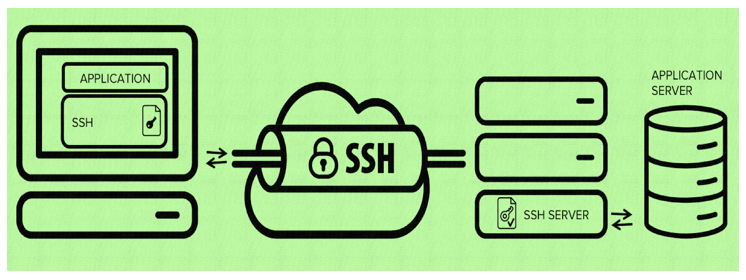
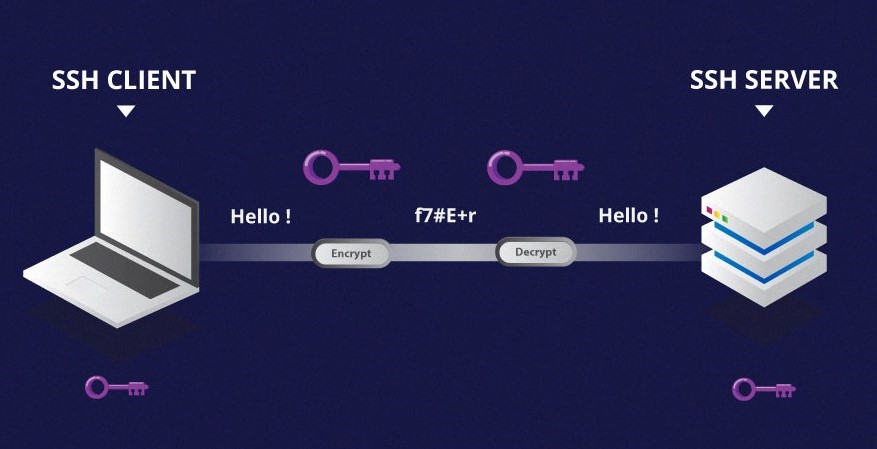
Secure Shell (SSH) is a network protocol that enables secure communication between two devices over an unsecured network. This protocol operates on the principle of public-key cryptography, offering robust authentication and encryption mechanisms. SSH’s core functionalities include:
- Secure Remote Login: SSH facilitates secure remote login to a server, allowing administrators to manage and access the system remotely.
- Secure File Transfer: The Secure Copy (SCP) and Secure File Transfer Protocol (SFTP) protocols, integrated within SSH, enable secure file transfer between systems.
- Secure Command Execution: SSH allows remote execution of commands on a server, facilitating automated tasks and system administration.
The Emergence of SSH on Windows Server
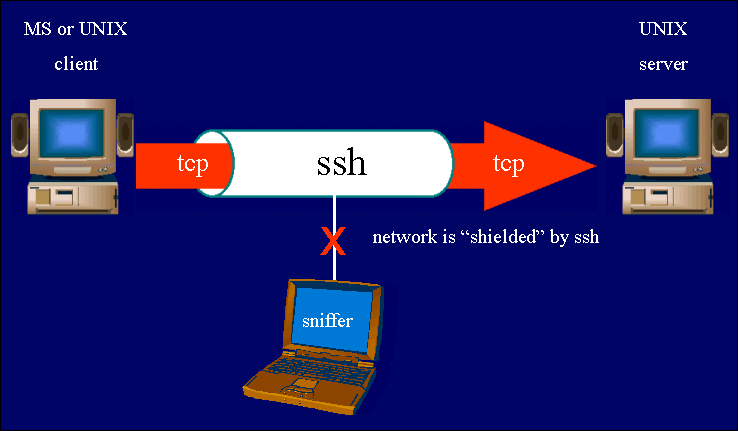
Historically, Windows Server relied on protocols like Remote Desktop Protocol (RDP) for remote administration. However, RDP operates on a less secure foundation, relying on password-based authentication and lacking inherent encryption capabilities. The integration of SSH into Windows Server 2025 addresses these vulnerabilities, providing a more secure and robust alternative for remote access and data transfer.
Benefits of Utilizing SSH on Windows Server 2025
The adoption of SSH on Windows Server 2025 brings forth a multitude of advantages, enhancing security, efficiency, and overall system management:
- Enhanced Security: SSH leverages public-key cryptography, providing a strong layer of security against unauthorized access and data interception. This is particularly crucial in environments where sensitive data is handled.
- Simplified Administration: SSH simplifies remote administration tasks, enabling administrators to manage servers from any location with a secure connection.
- Streamlined Deployment: SSH integrates seamlessly with existing network infrastructure, simplifying deployment and configuration.
- Improved Compatibility: SSH’s cross-platform compatibility allows for seamless communication between Windows and other operating systems, fostering a more unified environment.
- Increased Data Integrity: SSH ensures data integrity during transmission, safeguarding against tampering and ensuring the authenticity of transferred information.
Setting Up an SSH Server on Windows Server 2025
Setting up an SSH server on Windows Server 2025 involves a straightforward process, leveraging built-in features and readily available tools:
- Enabling the OpenSSH Server: Windows Server 2025 includes the OpenSSH server, a robust and widely used implementation of the SSH protocol. This server can be enabled through the Windows Server Manager or PowerShell.
- Configuring SSH Settings: Once enabled, the OpenSSH server requires configuration, including specifying the listening port, authentication methods, and access control rules.
- Generating SSH Keys: Public-key cryptography is at the core of SSH security. This requires generating a pair of keys: a public key for authentication and a private key for decryption.
- Configuring Firewall Rules: To allow incoming SSH connections, appropriate firewall rules need to be established, specifying the port and allowed IP addresses.
- Testing the SSH Connection: After setup, it is crucial to test the SSH connection to ensure proper functionality and security.
Security Considerations for SSH Servers
While SSH provides a robust security foundation, maintaining a secure environment requires ongoing vigilance:
- Strong Passwords and Key Management: Utilizing strong passwords and secure key management practices is paramount to prevent unauthorized access.
- Regular Security Updates: Keeping the SSH server and its underlying operating system updated with the latest security patches is crucial to address vulnerabilities.
- Access Control and User Management: Implementing strict access control policies and managing user accounts effectively are essential for preventing unauthorized access.
- Network Segmentation: Isolating the SSH server on a dedicated network segment can enhance security by limiting potential attack vectors.
Frequently Asked Questions (FAQs)
Q: What is the difference between SSH and RDP?
A: SSH and RDP are both remote access protocols, but they differ significantly in their security mechanisms. SSH leverages public-key cryptography for secure authentication and encryption, while RDP relies on password-based authentication and has limited encryption capabilities.
Q: Can I use SSH to transfer large files?
A: Yes, SSH supports secure file transfer through protocols like SCP and SFTP, making it suitable for transferring large files securely.
Q: How can I secure my SSH server against brute-force attacks?
A: Implement strong password policies, enable two-factor authentication, and utilize tools like Fail2ban to detect and block brute-force attempts.
Q: Is it safe to use SSH over a public Wi-Fi network?
A: While SSH provides strong encryption, using it over a public Wi-Fi network is not recommended. Consider using a VPN to create a secure tunnel for SSH traffic.
Tips for Effective SSH Server Management
- Enable SSH logging: Logging provides valuable insights into SSH activity, aiding in troubleshooting and security analysis.
- Regularly audit SSH server configurations: Periodically review and update SSH server configurations to ensure adherence to security best practices.
- Implement SSH tunneling for sensitive applications: SSH tunneling can create secure connections for applications that require a high level of security.
- Utilize SSH key management tools: Dedicated key management tools simplify the process of generating, storing, and managing SSH keys.
Conclusion
The integration of SSH servers into Windows Server 2025 signifies a significant step towards secure remote administration and data transfer. By leveraging the robust security features and functionalities of SSH, organizations can enhance their network security posture, simplify remote management tasks, and foster a more efficient and secure IT environment. As technology evolves, the importance of secure communication protocols like SSH will continue to grow, playing a pivotal role in safeguarding data and ensuring seamless and reliable remote access to critical systems.




Closure
Thus, we hope this article has provided valuable insights into Secure Shell (SSH) Server on Windows Server 2025: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!
