Securely Connecting to Windows: Exploring the Benefits and Implementation of SSH
Related Articles: Securely Connecting to Windows: Exploring the Benefits and Implementation of SSH
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Securely Connecting to Windows: Exploring the Benefits and Implementation of SSH. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Securely Connecting to Windows: Exploring the Benefits and Implementation of SSH

The Secure Shell (SSH) protocol has become an indispensable tool for secure remote access and management of computer systems. While traditionally associated with Linux and Unix environments, its utility has extended to Windows platforms, enhancing their security and manageability.
This article explores the significance of enabling SSH on Windows systems, delving into its functionalities, benefits, and implementation procedures.
Understanding the Power of SSH
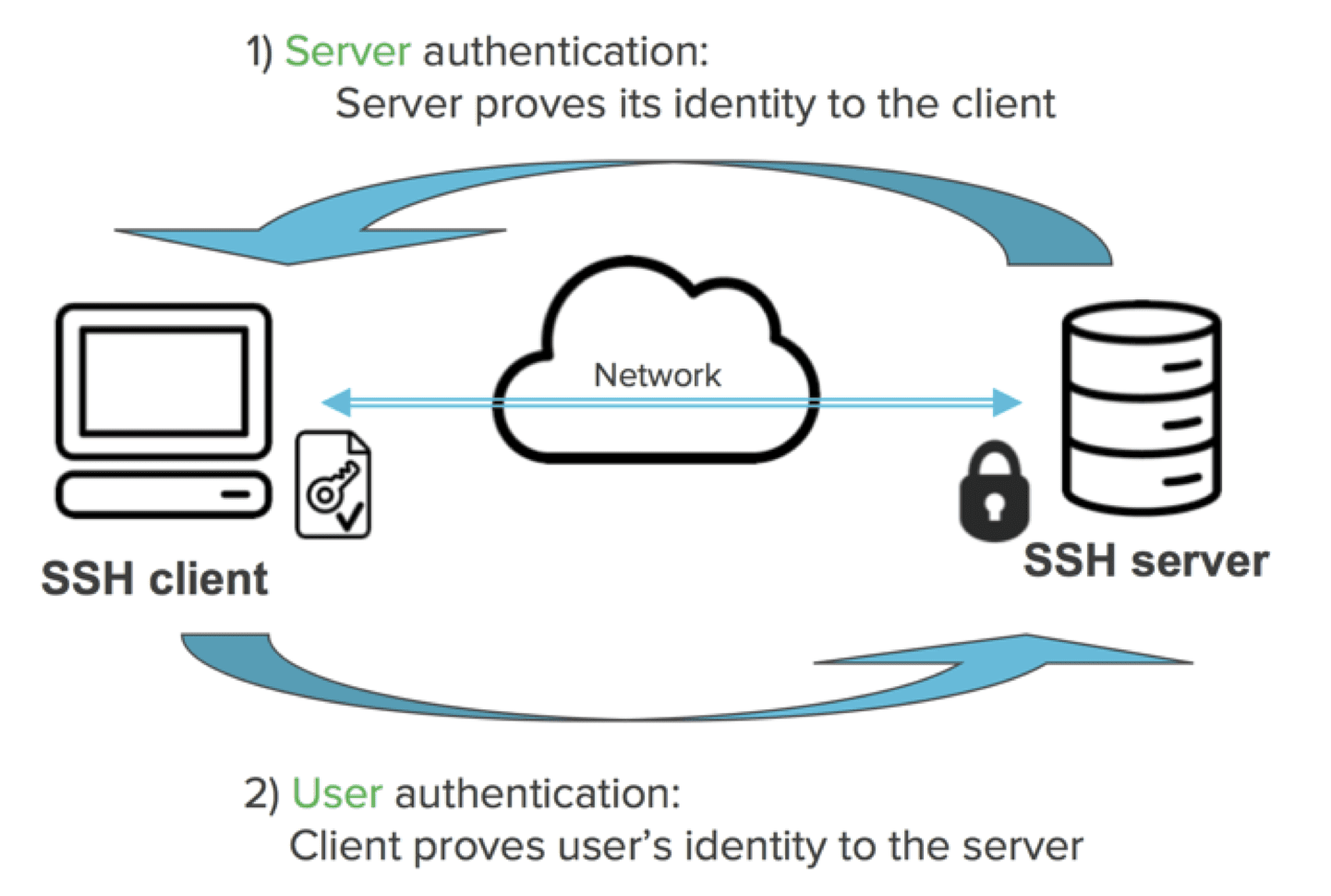
SSH is a cryptographic network protocol that allows secure communication between two devices over an unsecured network. It encrypts all data transmitted, including passwords, ensuring confidentiality and integrity. This makes it ideal for remote access, file transfer, and command execution, offering several advantages over traditional methods like Telnet or Remote Desktop Protocol (RDP).
Benefits of Enabling SSH on Windows
1. Enhanced Security: SSH employs strong cryptographic algorithms, including public-key cryptography, to secure data transmission. This significantly reduces the risk of unauthorized access and data breaches, making it a more secure alternative to traditional protocols like Telnet.
2. Remote Access and Management: SSH enables administrators to access and manage Windows systems remotely, regardless of physical location. This is particularly useful for troubleshooting, system updates, and configuration changes, streamlining IT operations.
3. Automated Scripting and Task Execution: SSH allows for the execution of automated scripts and commands on remote Windows systems. This automates repetitive tasks, saving time and reducing human error.
4. Secure File Transfer: SSH supports the Secure Copy (SCP) protocol, allowing for secure file transfer between systems. This ensures data integrity and confidentiality during file transfers, eliminating the risk of data corruption or interception.
5. Port Forwarding and Tunneling: SSH provides functionalities for port forwarding and tunneling, enabling secure access to specific services or applications on remote systems. This is particularly useful for accessing internal services from external networks.
Enabling SSH on Windows
Windows does not inherently support SSH. However, enabling SSH functionality on Windows systems can be achieved through various methods, including:
1. OpenSSH for Windows: OpenSSH is an open-source implementation of the SSH protocol that is available for Windows. It can be downloaded and installed directly from the official website or through the Microsoft Store. Once installed, OpenSSH provides a client and server component, allowing for both remote access and server functionality.
2. Windows Subsystem for Linux (WSL): WSL allows users to run Linux distributions directly on Windows. By installing a Linux distribution like Ubuntu or Debian within WSL, users can leverage the built-in SSH functionality of the Linux environment to access and manage Windows systems remotely.
3. Third-Party SSH Clients: Several third-party SSH clients are available for Windows, such as PuTTY and MobaXterm. These clients provide a graphical interface for connecting to SSH servers and managing remote systems.
Implementation Guide
Enabling OpenSSH for Windows:
- Download and Install OpenSSH: Download the OpenSSH package from the official website or the Microsoft Store.
- Install OpenSSH Server: During installation, select the "OpenSSH Server" option to enable SSH server functionality.
-
Configure OpenSSH Server: Open the "OpenSSH Server" configuration file (usually located at "C:Program FilesOpenSSHetcsshd_config") and modify the following settings:
- Port: Change the default port (22) if necessary.
- Password Authentication: Enable or disable password authentication as required.
- Key Authentication: Configure key-based authentication for enhanced security.
- Start OpenSSH Server: Start the OpenSSH server service using the "Services" application or the command line.
Enabling SSH through WSL:
- Install WSL: Enable the "Windows Subsystem for Linux" feature in Windows Settings.
- Install a Linux Distribution: Install a Linux distribution like Ubuntu or Debian through the Microsoft Store.
- Open a Linux Terminal: Launch the installed Linux distribution’s terminal.
- Install SSH Server: Use the package manager of the chosen Linux distribution to install the SSH server package (e.g., "sudo apt update && sudo apt install openssh-server" for Ubuntu).
- Configure SSH Server: Configure the SSH server settings within the Linux environment.
- Start SSH Server: Start the SSH server service using the command line (e.g., "sudo systemctl enable ssh" and "sudo systemctl start ssh").
Security Considerations
While SSH offers enhanced security, it is crucial to implement best practices to further strengthen the security of your Windows systems:
- Strong Passwords: Use strong, unique passwords for all user accounts and SSH access.
- Key-Based Authentication: Utilize key-based authentication instead of password authentication for enhanced security.
- Firewall Rules: Configure firewall rules to allow SSH access only from authorized sources.
- Regular Security Updates: Keep all operating systems and software up to date with the latest security patches.
- Regular Audits: Regularly audit your SSH configurations and access logs to detect and mitigate potential security risks.
FAQs
Q: What is the difference between SSH and RDP?
A: SSH is a protocol designed for secure command-line access and file transfer, while RDP is a protocol designed for remote desktop access, allowing users to control a remote computer’s graphical interface.
Q: Can I use SSH to access a Windows system from a Linux system?
A: Yes, you can use SSH to access a Windows system from a Linux system, provided the Windows system has SSH enabled.
Q: Is it safe to enable SSH on my Windows system?
A: Enabling SSH on your Windows system can enhance security, but it is essential to implement proper security measures, such as strong passwords, key-based authentication, and firewall rules, to mitigate potential risks.
Q: What are the common SSH ports?
A: The default SSH port is 22. However, you can configure the SSH server to use a different port for enhanced security.
Tips
- Use Key-Based Authentication: Consider using key-based authentication instead of password authentication for improved security.
- Limit Access: Restrict SSH access to specific IP addresses or user accounts to enhance security.
- Monitor Access Logs: Regularly monitor SSH access logs to detect any suspicious activity.
- Use a Strong SSH Client: Choose a reputable and secure SSH client for connecting to remote systems.
Conclusion
Enabling SSH on Windows systems significantly enhances security, manageability, and automation capabilities. By implementing SSH, administrators can securely access and manage remote Windows systems, automate tasks, and transfer files securely. With careful configuration and security measures, SSH can provide a robust and secure solution for remote access and management of Windows systems, making them more resilient and efficient.




Closure
Thus, we hope this article has provided valuable insights into Securely Connecting to Windows: Exploring the Benefits and Implementation of SSH. We thank you for taking the time to read this article. See you in our next article!
