The Future of Security: Exploring the Role of TPM in Windows 2025
Related Articles: The Future of Security: Exploring the Role of TPM in Windows 2025
Introduction
With great pleasure, we will explore the intriguing topic related to The Future of Security: Exploring the Role of TPM in Windows 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Future of Security: Exploring the Role of TPM in Windows 2025
The landscape of computing is constantly evolving, with new technologies and security threats emerging at a rapid pace. As we approach the release of Windows 2025, it is crucial to understand the role of security features like the Trusted Platform Module (TPM) in shaping the future of computing. While Microsoft has not officially confirmed specific requirements for Windows 2025, the growing importance of TPM in modern operating systems suggests it will likely play a significant role.
Understanding the Trusted Platform Module (TPM)
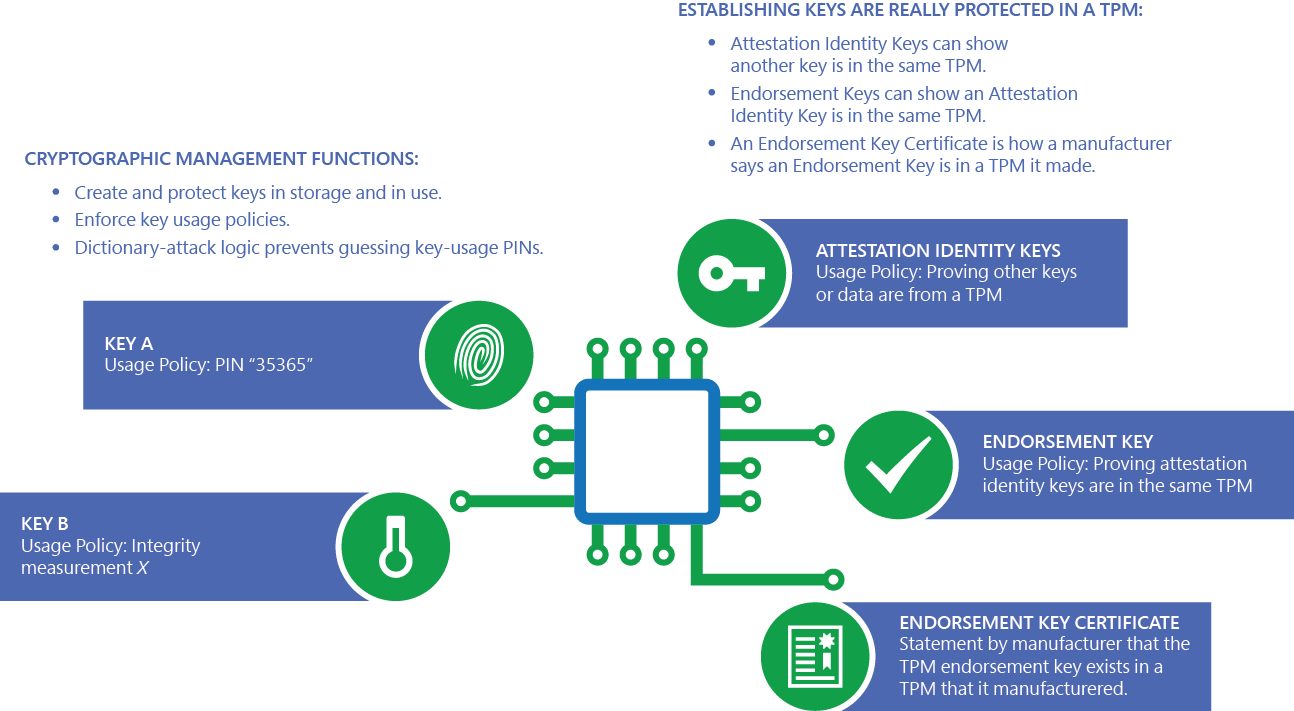
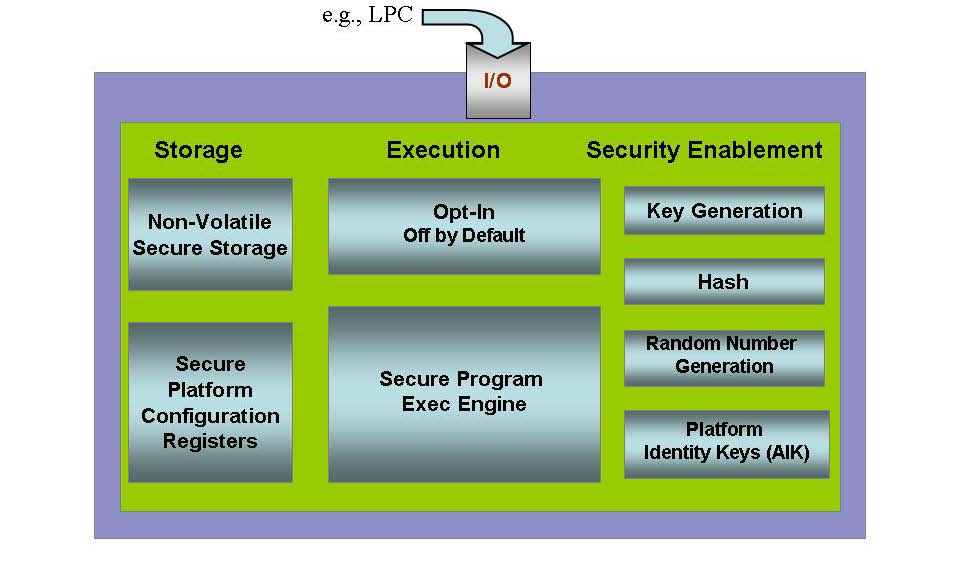
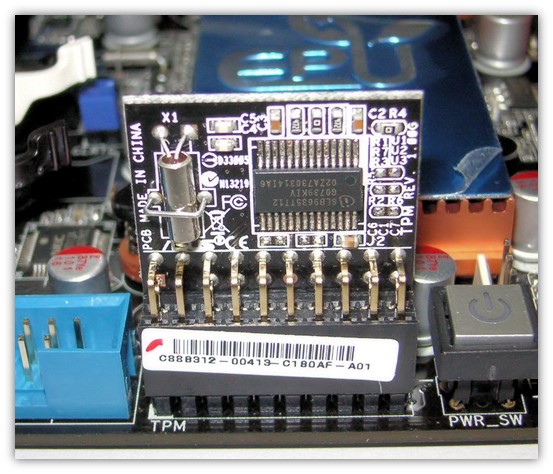
The TPM is a dedicated hardware chip embedded on the motherboard of a computer. It acts as a secure enclave, responsible for storing and protecting sensitive cryptographic keys and other security data. This isolated environment makes it difficult for malicious software to access or tamper with these crucial elements.
Benefits of TPM Integration:
The integration of TPM in modern operating systems offers numerous benefits:
- Enhanced Boot Security: TPM facilitates secure boot, ensuring that only authorized operating systems and drivers can load at startup. This significantly reduces the risk of malware infection during the boot process.
- Stronger Encryption: TPM enables hardware-based encryption, allowing for more secure storage of sensitive data like passwords, user credentials, and encryption keys. This protection extends beyond the operating system itself, safeguarding data even if the operating system is compromised.
- Secure Identity Management: TPM plays a vital role in secure identity management, verifying the authenticity of devices and users. This is crucial for authentication and authorization, especially in enterprise environments.
- Improved Device Integrity: TPM helps to ensure the integrity of the device, detecting any unauthorized hardware or software changes. This feature enhances overall system security by preventing malicious modifications.
- Enhanced Privacy: TPM contributes to enhanced privacy by protecting sensitive data from unauthorized access, even if the device is lost or stolen.
The Future of Windows and TPM:
While the exact requirements for Windows 2025 remain unknown, the increasing focus on security and privacy within the tech industry suggests that TPM integration will likely be crucial. As cyberattacks become more sophisticated, the need for robust security measures like TPM becomes increasingly critical.
FAQs:
1. What is the difference between a TPM 1.2 and a TPM 2.0 chip?
TPM 2.0 is the latest version of the standard, offering significant improvements over its predecessor, TPM 1.2. It features enhanced security algorithms, increased storage capacity, and more robust platform authentication capabilities.
2. Do all motherboards have a TPM chip?
Not all motherboards come equipped with a TPM chip. Some older motherboards might not have this feature. However, most modern motherboards include a TPM chip, either directly on the motherboard or as a separate module.
3. Can I add a TPM chip to my computer if it doesn’t have one?
In some cases, you can add a TPM chip to your computer if it doesn’t have one. However, this requires a compatible motherboard and might involve some technical expertise.
4. Is TPM mandatory for Windows 10?
While TPM is not strictly mandatory for Windows 10, it is highly recommended for enhanced security. Some features, like BitLocker encryption, require a TPM chip for full functionality.
5. What happens if my computer doesn’t have a TPM chip?
If your computer doesn’t have a TPM chip, you might not be able to utilize some of the advanced security features offered by Windows 2025. You might also face limitations in accessing certain online services or applications that rely on TPM-based authentication.
Tips for Utilizing TPM:
- Enable TPM in BIOS: Ensure that the TPM chip is enabled in your computer’s BIOS settings.
- Update Firmware: Regularly update your TPM firmware to benefit from the latest security enhancements.
- Utilize TPM-enabled features: Take advantage of features like BitLocker encryption, secure boot, and Windows Hello for enhanced security.
- Stay informed: Keep yourself updated on the latest developments in TPM technology and its role in future operating systems.
Conclusion:
The integration of TPM in future operating systems like Windows 2025 is a crucial step towards enhancing security and protecting user data. As technology continues to evolve and cyber threats become more sophisticated, TPM will play a vital role in securing the digital landscape. By understanding the benefits of TPM and implementing its features, users can significantly improve their online security and safeguard their data in an increasingly interconnected world.





Closure
Thus, we hope this article has provided valuable insights into The Future of Security: Exploring the Role of TPM in Windows 2025. We appreciate your attention to our article. See you in our next article!
