The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025
Related Articles: The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025
- 2 Introduction
- 3 The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025
- 3.1 Understanding Trusted Platform Modules (TPMs)
- 3.2 The Significance of TPMs in Windows Server 2025
- 3.3 Exploring the Potential of TPMs in Windows Server 2025:
- 3.4 FAQs:
- 3.5 Tips for Implementing TPMs in Windows Server 2025:
- 3.6 Conclusion:
- 4 Closure
The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025

The digital landscape is evolving at a rapid pace, with increasing reliance on cloud services and interconnected devices. This evolution brings with it a growing concern for cybersecurity, demanding robust measures to safeguard sensitive data and critical infrastructure. Enter Trusted Platform Modules (TPMs), a hardware-based security component poised to play a pivotal role in securing future computing environments, including Windows Server 2025.
Understanding Trusted Platform Modules (TPMs)
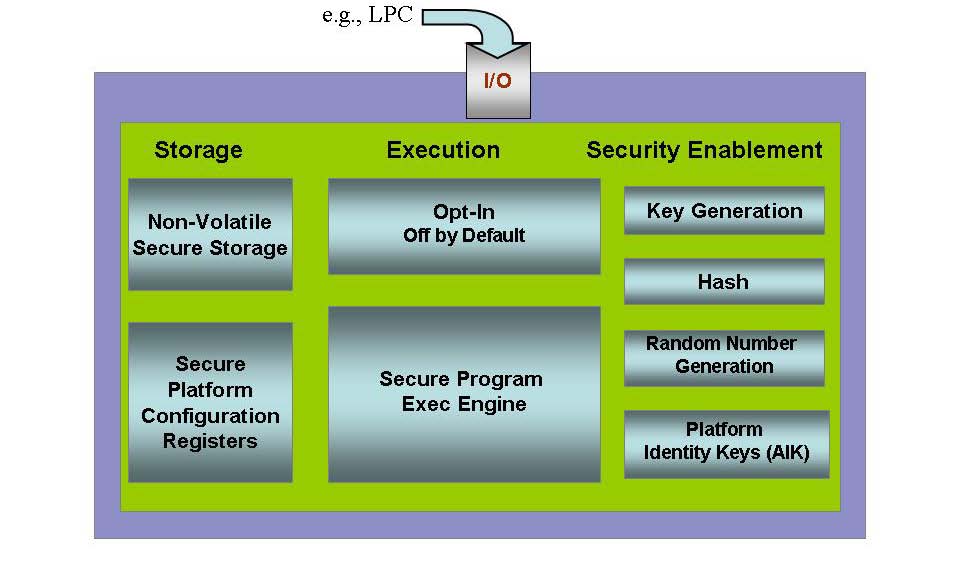
A TPM is a dedicated cryptographic processor embedded within a computer system, acting as a secure vault for sensitive data and cryptographic keys. It operates independently from the main CPU, ensuring its security is not compromised by malware or other vulnerabilities within the operating system.
Here’s a breakdown of key features and functionalities of TPMs:
- Secure Storage: TPMs provide a secure storage mechanism for sensitive data, such as encryption keys, passwords, and digital certificates. This storage is tamper-resistant, ensuring data integrity and confidentiality.
- Hardware-based Encryption: TPMs perform cryptographic operations, such as encryption and decryption, directly on the hardware level. This eliminates the risk of software vulnerabilities compromising the security of sensitive data.
- Secure Boot: TPMs play a crucial role in secure boot processes, verifying the authenticity of the operating system and other critical system components before allowing them to load. This mitigates the risk of malicious bootloaders or malware compromising the system at the earliest stages of startup.
- Measurement and Attestation: TPMs can measure the state of the system, including software and hardware components, and generate a unique digital fingerprint or attestation. This enables remote verification of system integrity and authenticity, enhancing trust in cloud environments and device management.
The Significance of TPMs in Windows Server 2025
The integration of TPMs in Windows Server 2025 (a hypothetical future release) will be crucial for bolstering security and enhancing trust across various aspects of the operating system and server infrastructure. Here’s a look at some key benefits:
- Enhanced Security for Virtual Machines: TPMs can be utilized to secure virtual machines, protecting sensitive data and applications running within them. This is especially relevant for cloud environments where multiple tenants share the same physical hardware.
- Improved Data Encryption: TPMs can be used to encrypt data at rest, ensuring that even if a server is compromised, the data remains inaccessible to unauthorized individuals. This is crucial for protecting sensitive data, such as customer information, financial records, and intellectual property.
- Strengthened Identity Management: TPMs can be leveraged to secure identity management systems, providing a more robust and tamper-resistant mechanism for verifying user identities and granting access to sensitive resources.
- Enhanced Platform Integrity: TPMs play a vital role in verifying the integrity of the operating system and other critical components, ensuring that only authorized and trustworthy software is loaded and executed. This helps mitigate the risk of malware infection and system compromise.
- Improved Trust in Cloud Environments: TPMs provide a mechanism for verifying the authenticity and integrity of cloud services and infrastructure. This enhances trust in cloud environments and enables organizations to securely migrate sensitive workloads to the cloud.
Exploring the Potential of TPMs in Windows Server 2025:
While TPMs are already widely deployed in modern computing devices, their adoption in Windows Server 2025 could lead to significant advancements in security and trust, particularly in the following areas:
- Secure Enclaves: Windows Server 2025 could leverage TPMs to create secure enclaves, isolated environments within the server where sensitive operations can be performed with enhanced security. This could be utilized for critical tasks like key management, secure code execution, and protecting sensitive data from unauthorized access.
- Zero Trust Security: TPMs can play a key role in implementing zero-trust security models, where every device and user is authenticated and authorized before accessing sensitive resources. This approach eliminates the implicit trust inherent in traditional security models, significantly enhancing security posture.
- Enhanced Virtualization Security: TPMs can be used to secure virtual machine environments, providing a more robust and tamper-resistant mechanism for isolating virtual machines and preventing unauthorized access to sensitive data. This is particularly important for cloud environments where multiple tenants share the same physical hardware.
- Secure Boot for Hypervisors: TPMs can be utilized to secure the boot process of hypervisors, the software responsible for managing virtual machines. This ensures that only authorized and trustworthy hypervisors are loaded, mitigating the risk of malicious hypervisors compromising the entire virtualized environment.
- Advanced Threat Detection: TPMs can be used to monitor system activity and detect suspicious behavior, providing early warning of potential threats and enabling faster response times. This can be particularly useful for detecting and mitigating advanced persistent threats (APTs), which are often difficult to detect using traditional security measures.
FAQs:
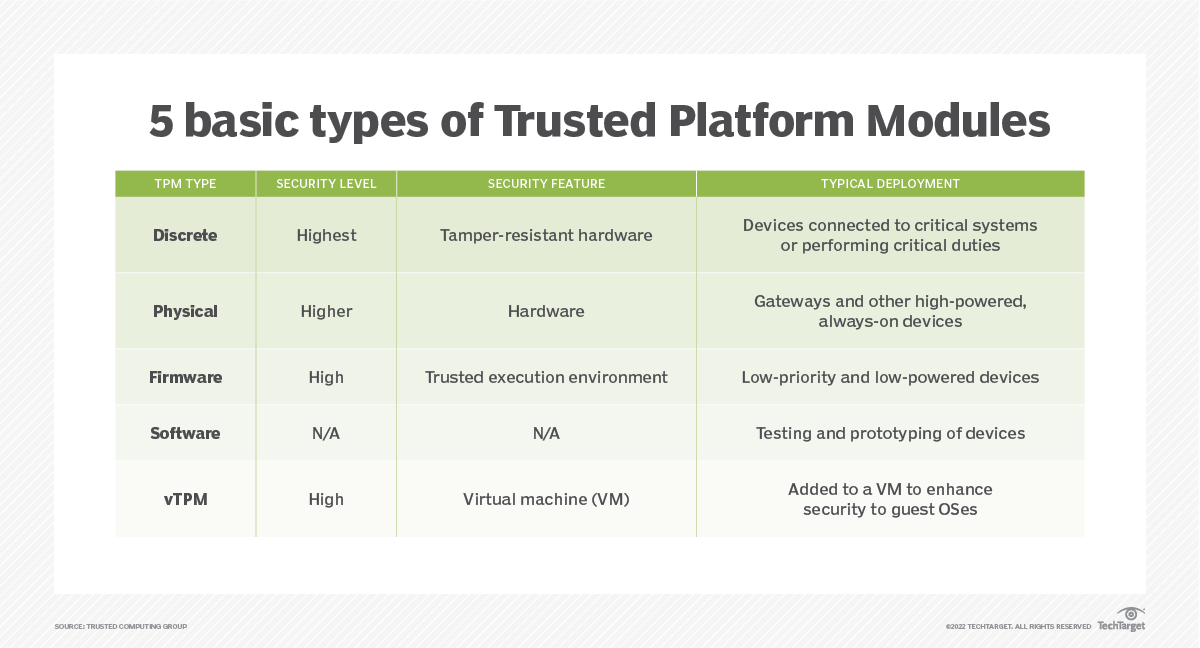
Q: What are the different types of TPMs available?
A: There are two main types of TPMs:
- Discrete TPM: A separate chip dedicated to TPM functionality. This offers higher security and isolation compared to integrated TPMs.
- Integrated TPM: A TPM functionality integrated into the chipset or motherboard. While less secure than discrete TPMs, they are often more cost-effective and widely available.
Q: How can I check if my system has a TPM?
A: You can check for the presence of a TPM using the following methods:
- Windows Settings: Go to "System" -> "About" and check for the "Trusted Platform Module" entry.
- Command Prompt: Run the command "tpm.msc" to open the TPM Management Console.
- BIOS Settings: Check the BIOS settings for a "TPM" or "Security Device" option.
Q: What are the security implications of using a TPM?
A: TPMs provide a significant boost to system security by:
- Protecting sensitive data: TPMs provide secure storage for sensitive data like encryption keys, passwords, and digital certificates.
- Strengthening authentication: TPMs can be used to verify user identities and prevent unauthorized access to sensitive resources.
- Enhancing platform integrity: TPMs help ensure that only authorized and trustworthy software is loaded and executed, mitigating the risk of malware infection.
Q: Are there any drawbacks to using TPMs?
A: While TPMs offer significant security benefits, they also have some limitations:
- Complexity: Implementing and managing TPMs can be complex, requiring expertise in cryptography and security best practices.
- Compatibility: Not all systems and software are compatible with TPMs, which can pose challenges during deployment and migration.
- Cost: TPMs can add to the overall cost of a system, especially for discrete TPMs.
Q: What are the future implications of TPMs in Windows Server 2025?
A: The integration of TPMs in Windows Server 2025 is expected to significantly enhance security and trust in the operating system and server infrastructure, particularly in cloud environments.
Q: How can I prepare for the adoption of TPMs in Windows Server 2025?
A: Here are some steps you can take:
- Evaluate your current security posture: Determine your current reliance on hardware-based security and identify areas where TPMs can enhance your security.
- Familiarize yourself with TPM technologies: Learn about different TPM types, their functionalities, and how they can be integrated into your systems.
- Develop a strategy for TPM deployment: Plan how you will deploy and manage TPMs across your organization, considering compatibility, security policies, and training requirements.
Tips for Implementing TPMs in Windows Server 2025:
- Choose the right TPM type: Select the TPM type that best suits your security requirements and budget, considering the level of security and isolation you need.
- Ensure compatibility: Verify that your hardware and software are compatible with TPMs before deploying them.
- Establish clear security policies: Define clear policies for managing and using TPMs, including key management, access control, and auditing.
- Provide adequate training: Train your IT staff on how to deploy, manage, and troubleshoot TPMs.
- Stay informed about security best practices: Keep abreast of evolving security threats and best practices for using TPMs effectively.
Conclusion:
Trusted Platform Modules are poised to play a crucial role in securing future computing environments, including Windows Server 2025. Their ability to provide hardware-based security, enhance data encryption, and strengthen platform integrity offers significant benefits for organizations looking to protect sensitive data and critical infrastructure. While implementing and managing TPMs requires careful planning and expertise, the benefits they offer in terms of enhanced security and trust make them an essential component of any robust cybersecurity strategy. As the digital landscape continues to evolve, TPMs will become increasingly important for safeguarding sensitive data and ensuring the integrity of computing systems. By embracing these technologies and implementing them effectively, organizations can significantly enhance their security posture and build a more secure and trustworthy digital future.



Closure
Thus, we hope this article has provided valuable insights into The Future of Security: Exploring the Role of Trusted Platform Modules in Windows Server 2025. We thank you for taking the time to read this article. See you in our next article!
