The Shift Towards Enhanced Security: Understanding the Significance of TPM in Server 2025
Related Articles: The Shift Towards Enhanced Security: Understanding the Significance of TPM in Server 2025
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Shift Towards Enhanced Security: Understanding the Significance of TPM in Server 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Shift Towards Enhanced Security: Understanding the Significance of TPM in Server 2025
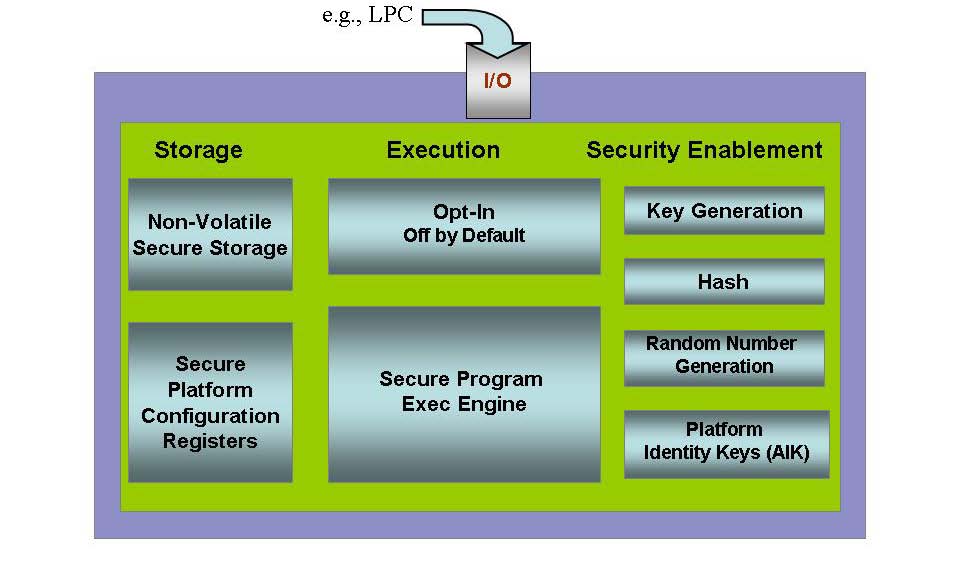
The landscape of technology is constantly evolving, and with it, the need for robust security measures. In this context, Microsoft’s decision to mandate the use of Trusted Platform Modules (TPMs) in Server 2025 signifies a significant shift towards enhanced security for both hardware and software. This article delves into the reasons behind this requirement, exploring the benefits it brings and addressing common questions surrounding TPM adoption.
What is a TPM and Why is it Important?
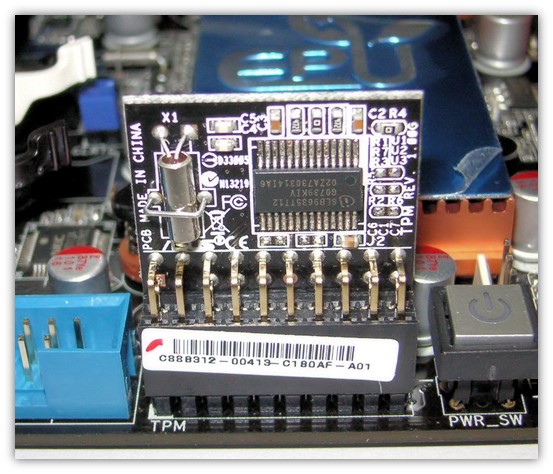
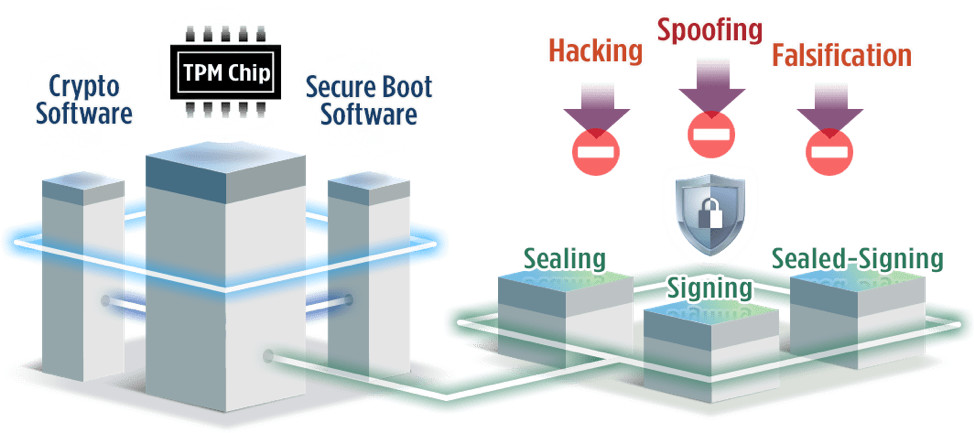
A Trusted Platform Module (TPM) is a dedicated cryptographic processor embedded on a computer motherboard. It acts as a hardware-based security key, providing a secure environment for storing and managing cryptographic keys, passwords, and other sensitive data.
The Security Advantages of TPM Integration in Server 2025:
- Secure Boot: TPMs enable secure boot, a process that verifies the integrity of the operating system and other critical software before they are loaded. This prevents malicious software from loading and compromising the system.
- Enhanced Encryption: TPMs facilitate hardware-level encryption, ensuring that data stored on the server remains secure even if the server is physically compromised.
- Stronger Authentication: TPMs can be used for secure authentication, verifying the identity of users and devices attempting to access the server.
- Improved Code Signing: TPMs enhance code signing by providing a secure environment for storing and verifying digital signatures, ensuring the authenticity and integrity of software.
- Protection against Malware: TPMs offer a robust defense against malware by preventing the execution of unauthorized or malicious code.
- Compliance with Security Standards: The use of TPMs aligns with industry-standard security regulations and best practices, demonstrating a commitment to data security and compliance.
Addressing Common Questions about TPM in Server 2025:
Q: What are the specific benefits of TPM in Server 2025?
A: TPMs in Server 2025 offer a comprehensive approach to security, encompassing secure boot, enhanced encryption, stronger authentication, improved code signing, and protection against malware. This multi-faceted security approach significantly strengthens the overall security posture of the server environment.
Q: Is TPM mandatory for all Server 2025 installations?
A: While Microsoft strongly recommends the use of TPMs, it is not strictly mandatory for all Server 2025 installations. However, certain features and functionalities, such as secure boot, may require a TPM for optimal security.
Q: What are the potential challenges associated with TPM adoption?
A: The primary challenge associated with TPM adoption is the need for hardware compatibility. Older servers may not have a built-in TPM, requiring an upgrade or a separate hardware solution. Additionally, some organizations may need to update their security policies and procedures to fully leverage the capabilities of TPMs.
Q: How can organizations prepare for the integration of TPMs in Server 2025?
A: Organizations should begin by assessing their current hardware infrastructure and identifying servers that do not have a TPM. They should then develop a plan for upgrading or replacing these servers with TPM-enabled models. It is also crucial to educate IT staff about the benefits of TPMs and how to effectively utilize their capabilities.
Tips for Implementing TPMs in Server 2025:
- Prioritize TPM-enabled hardware: When purchasing new servers, prioritize models that have a built-in TPM.
- Evaluate existing hardware: Assess existing servers to identify those that lack TPM support and plan for upgrades or replacements.
- Train IT staff: Provide comprehensive training to IT staff on TPM functionalities and their implications for security.
- Review security policies: Update security policies to incorporate TPM-related best practices and enhance overall security posture.
- Leverage available resources: Utilize Microsoft documentation and other resources to gain a deeper understanding of TPMs and their implementation.
Conclusion:
The integration of TPMs in Server 2025 represents a significant step towards enhanced security in the evolving digital landscape. By leveraging the capabilities of TPMs, organizations can strengthen their security posture, protect sensitive data, and comply with industry-standard security regulations. While the transition to TPM-enabled servers may present some challenges, the long-term benefits in terms of security and data integrity far outweigh the initial hurdles. By proactively addressing these challenges and implementing TPMs effectively, organizations can ensure the security and integrity of their critical server infrastructure.



Closure
Thus, we hope this article has provided valuable insights into The Shift Towards Enhanced Security: Understanding the Significance of TPM in Server 2025. We appreciate your attention to our article. See you in our next article!
