Understanding the Significance of Key Management Systems (KMS) in 2025
Related Articles: Understanding the Significance of Key Management Systems (KMS) in 2025
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Understanding the Significance of Key Management Systems (KMS) in 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding the Significance of Key Management Systems (KMS) in 2025
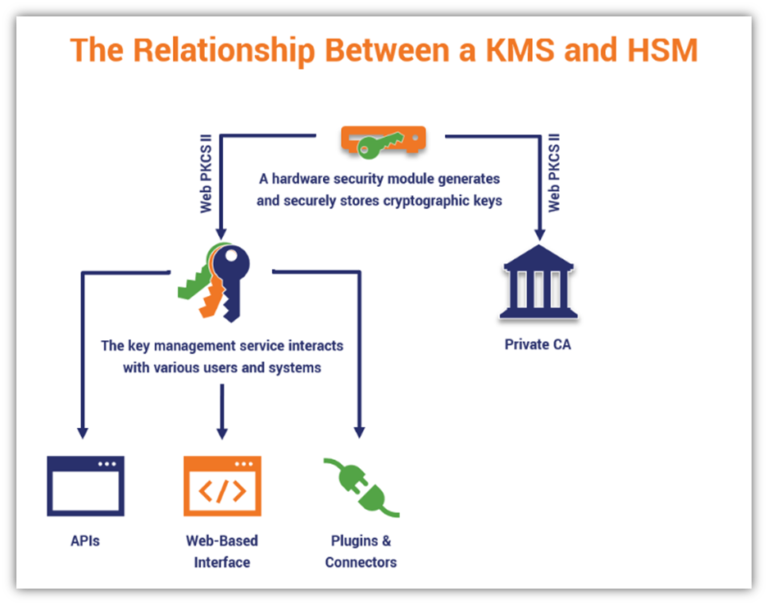
The landscape of digital security is constantly evolving, with threats becoming increasingly sophisticated and pervasive. In this dynamic environment, robust key management is paramount for safeguarding sensitive information and maintaining operational integrity. Key Management Systems (KMS) are essential tools for organizations of all sizes, enabling them to securely manage cryptographic keys – the building blocks of modern security protocols.
As we approach 2025, the importance of KMS is only set to grow, driven by several key factors:
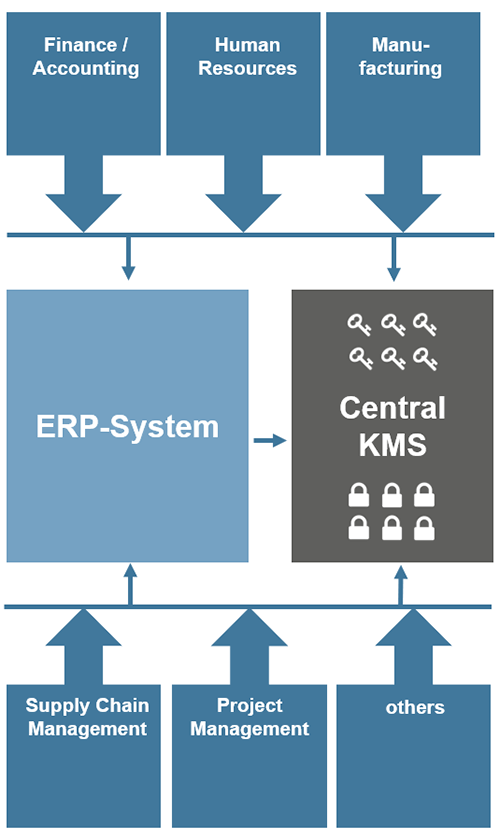
1. The Rise of Cloud Computing and Hybrid Environments: Organizations are increasingly adopting cloud-based solutions and hybrid infrastructure models. This necessitates a centralized and secure approach to key management that can seamlessly integrate across diverse environments.
2. Expanding Regulatory Compliance: Stricter data privacy regulations like GDPR and CCPA are driving the need for enhanced data protection, including the secure management of cryptographic keys. KMS solutions provide the necessary compliance framework, ensuring that sensitive data is handled responsibly and securely.
3. The Proliferation of IoT and Edge Computing: The growing number of connected devices and the increasing reliance on edge computing amplify the need for secure key management. KMS solutions can effectively manage keys across a distributed network, ensuring that data remains protected even at the edge.
4. The Growing Threat of Cyberattacks: The constant evolution of cyber threats necessitates a proactive approach to security. KMS solutions provide a robust foundation for protecting sensitive data, enabling organizations to mitigate risks and respond effectively to evolving threats.
5. The Need for Scalability and Agility: Organizations require key management solutions that can scale with their evolving needs and adapt to changing security landscapes. Modern KMS solutions offer flexible and scalable architectures, ensuring that they can meet the demands of a dynamic digital environment.
Understanding KMS: Core Components and Functionality
A KMS typically consists of several key components, each playing a crucial role in securing and managing cryptographic keys:
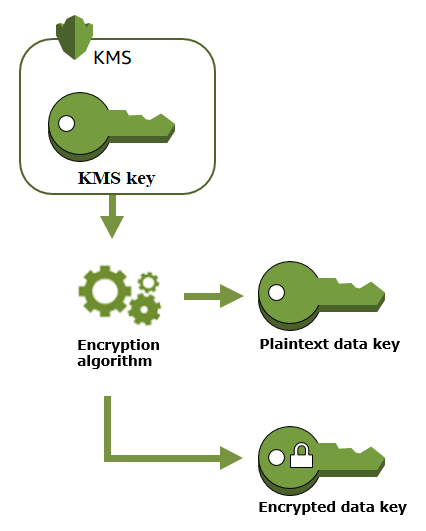
- Key Generation: KMS solutions generate strong cryptographic keys using robust algorithms and secure random number generators.
- Key Storage: Keys are stored in secure hardware security modules (HSMs) or other secure repositories, protected from unauthorized access.
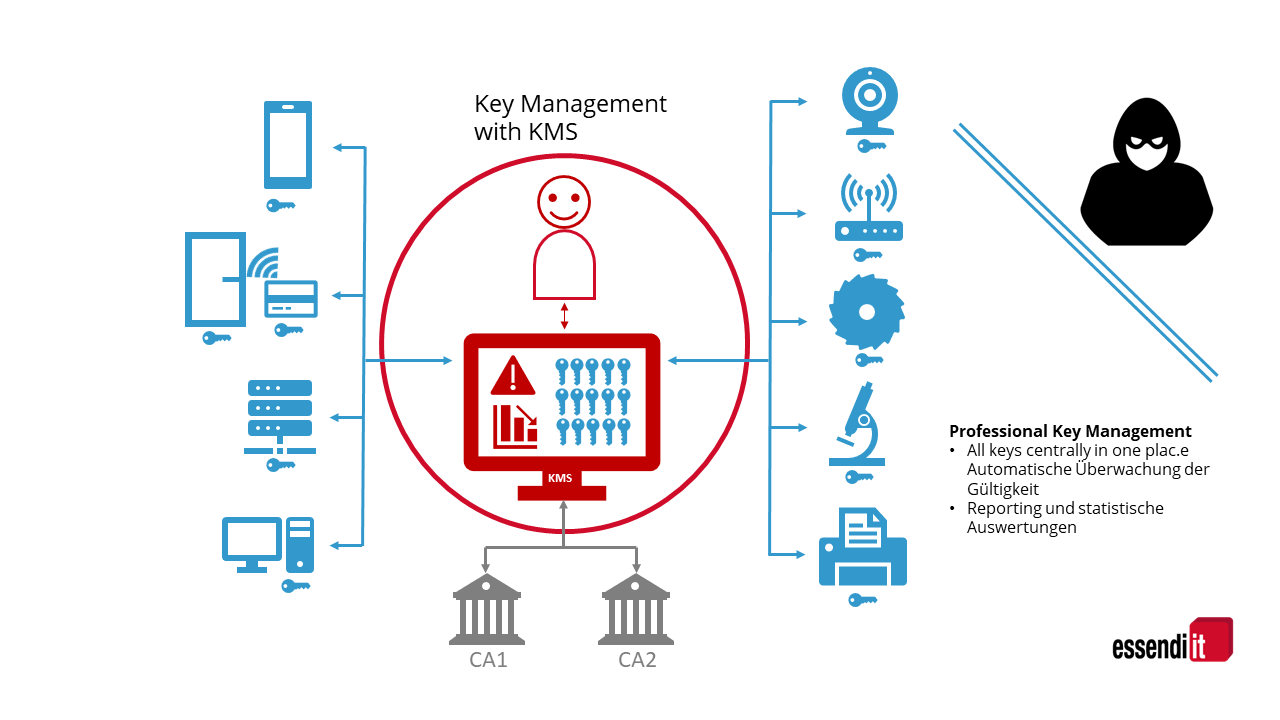
- Key Usage Control: KMS solutions implement strict access control mechanisms, ensuring that only authorized users or applications can access and use specific keys.
- Key Rotation and Revocation: Regular key rotation and revocation mechanisms are essential to minimize the risk of key compromise. KMS solutions automate these processes, ensuring continuous security.
- Auditing and Logging: KMS solutions maintain detailed audit logs, providing a comprehensive record of key access, usage, and modifications, enabling compliance and security investigations.
Benefits of Implementing a KMS
Implementing a robust KMS offers significant benefits for organizations, including:
- Enhanced Data Security: KMS solutions provide a secure foundation for protecting sensitive data, minimizing the risk of unauthorized access or data breaches.
- Simplified Key Management: KMS solutions automate key management processes, reducing the burden on IT staff and minimizing the potential for human error.
- Improved Compliance: KMS solutions facilitate compliance with various data privacy and security regulations, ensuring that organizations meet regulatory requirements.
- Enhanced Operational Efficiency: KMS solutions streamline key management processes, improving operational efficiency and reducing the time and resources required for security tasks.
- Reduced Risk of Key Compromise: KMS solutions implement robust security measures, reducing the risk of key compromise and mitigating the potential impact of data breaches.
FAQs on Key Management Systems
Q: What are the different types of KMS solutions available?
A: KMS solutions come in various forms, including hardware-based solutions (HSMs), software-based solutions, and cloud-based solutions. The choice of solution depends on factors such as the organization’s specific needs, security requirements, and budget.
Q: What are the key considerations when choosing a KMS solution?
A: Key considerations include the solution’s security features, scalability, compliance capabilities, integration with existing systems, and overall cost.
Q: How do I ensure that my KMS solution is secure?
A: Choose a KMS solution from a reputable vendor with a strong track record in security. Implement robust security measures, such as multi-factor authentication, access control lists, and regular security audits.
Q: What are the best practices for using a KMS?
A: Implement strong key generation and storage practices, enforce strict access controls, rotate keys regularly, and maintain comprehensive audit logs.
Tips for Implementing a KMS
- Start with a comprehensive assessment: Evaluate your organization’s security needs and identify key vulnerabilities.
- Choose the right solution: Select a KMS solution that meets your specific requirements and integrates seamlessly with your existing systems.
- Implement a robust security policy: Define clear policies for key management, access control, and auditing.
- Train your team: Ensure that your IT staff is properly trained on the use and management of the KMS solution.
- Monitor and evaluate: Regularly monitor the KMS solution’s performance, identify potential vulnerabilities, and make necessary adjustments.
Conclusion
In the rapidly evolving digital landscape, robust key management is essential for safeguarding sensitive data and maintaining operational integrity. KMS solutions provide a critical foundation for securing cryptographic keys, ensuring that organizations can protect their data from evolving threats. By understanding the benefits and best practices associated with KMS, organizations can effectively implement and leverage these solutions to enhance their security posture and mitigate risks in the digital age.



Closure
Thus, we hope this article has provided valuable insights into Understanding the Significance of Key Management Systems (KMS) in 2025. We thank you for taking the time to read this article. See you in our next article!
